This article is part of the Criminal Information System Management series, cybercriminal strategic positionning section.
Key Takeaways
- Understanding criminal organizations’ make-or-buy decisions reveals optimal intervention points. Disrupting externalized services (initial access brokers, cryptocurrency mixers) creates higher organizational costs than targeting internal capabilities.
- Market-oriented governance dominates standardized transactions (Initial Access Broker markets), hierarchical governance emerges for high asset specificity operations (APT groups), and hybrid forms balance coordination with incentive intensity (Ransomware-as-a-Service platforms).
- APT groups favor hierarchical, vertically integrated structures due to state backing reducing transaction costs, while profit-driven groups adopt market-based CaaS models, requiring different defensive strategies and threat modeling approaches
- Conti’s corporate mimicry strategy and LockBit’s >80% affiliate failure rate demonstrate cognitive limitations driving organizational choices, while creating defensive opportunities through information asymmetry exploitation.
- Opportunistic behavior needs sophisticated governance mechanisms. Criminal organizations develop reputation systems, escrow services, and internal monitoring structures to mitigate hold-up problems, creating vulnerabilities for targeted disruption strategies.
1. Introduction
For-profit cybercriminals and state-sponsored Advanced Persistent Threat (APT) both demonstrate predictable organizational evolution patterns responding to environmental changes.
With 65-100 employees, departmental hierarchies, HR processes, and $140,000 monthly operational costs, Conti exemplified a fundamental shift in criminal organization (globalcrime, apwg). This corporate criminalization reflects rational economic choices governed by transaction cost considerations. Where traditional criminology focuses on deviant behavior, this analysis reveals cybercriminals as economic actors making strategic organizational boundary decisions. The implications are profound as understanding criminal organizations through transaction cost economics provides unprecedented insights into their structural evolution, operational vulnerabilities, and defensive countermeasures.
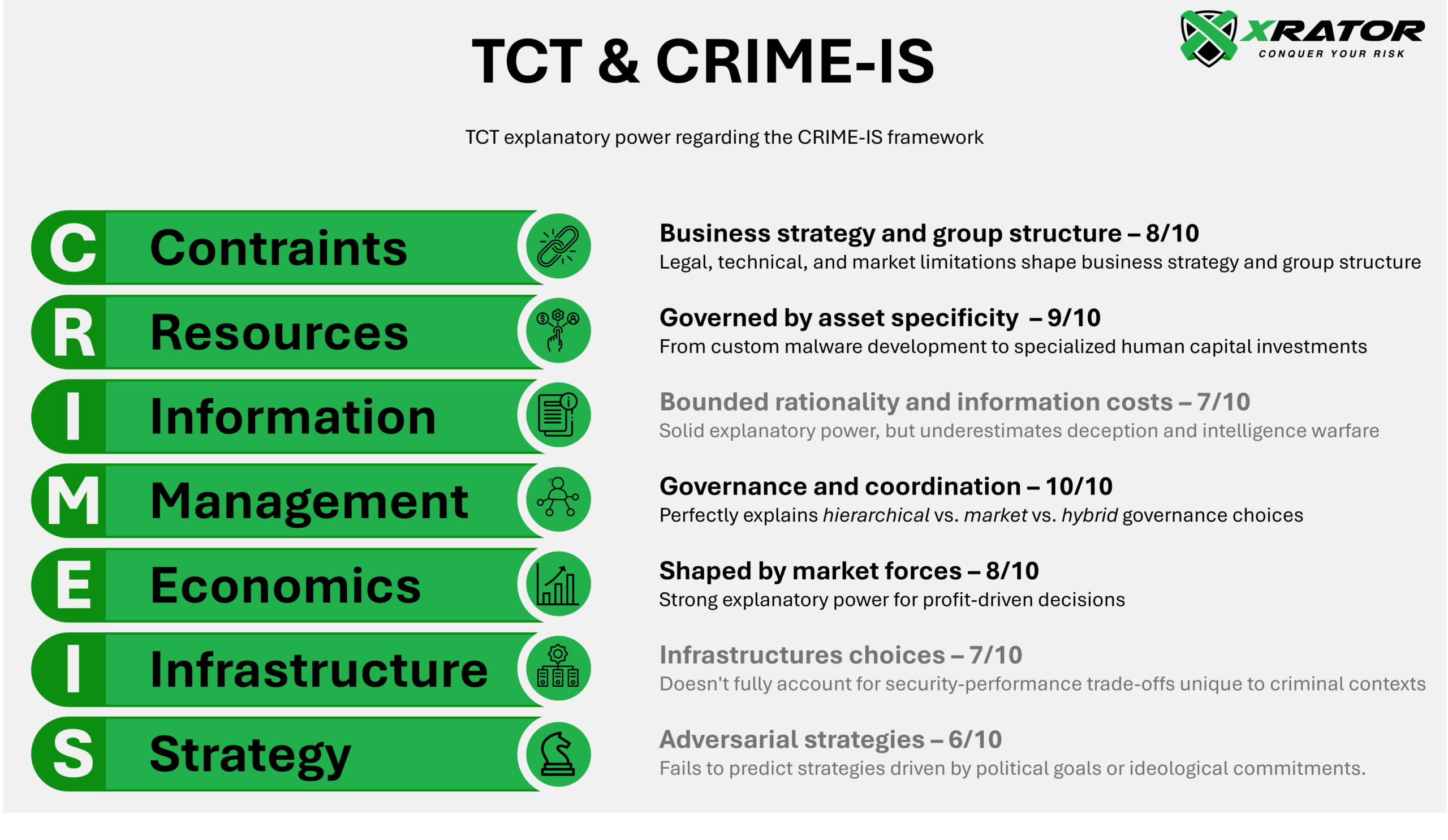
This article applies Oliver Williamson’s Transaction Cost Theory (TCT) to cybercriminal organizational behavior, demonstrating how profit-driven cybercrime groups and state-sponsored APT organizations make rational boundary decisions based on asset specificity, transaction frequency, uncertainty, and opportunism (ijim – AI-generated). Through analysis of major groups including, we establish that perpetrators face classic make-or-buy decisions, choosing between market-based transactions and hierarchical governance structures (tis).
Key findings highligth specialized criminal skills have limited transferability to legitimate employment, creating strong incentives for continued criminal association.
2. Theoretical Synthesis
Transaction Cost Theory provides a rigorous framework for understanding organizational boundaries through three fundamental dimensions that determine governance structure efficiency (jle, smj) :
- Asset specificity : The degree to which an investment cannot be redeployed.
- Uncertainty : The unpredictability surrounding transactions.
- Frequency : How often transactions recur.
A transaction is whenever something valuable moves from one party to another across a boundary. A boundary is the line that separe a ‘make’ choice or a ‘buy’ choice, influenced by cost, complexity, trust or control considerations.
Williamson’s discriminating alignment hypothesis posits that transactions are aligned with governance structures in a discriminating way, creating predictable patterns of make-versus-buy decisions.
These parameters interact to determine optimal governance forms: market governance for low asset specificity transactions with competitive alternatives; hierarchical governance for high asset specificity requiring coordinated adaptation; and hybrid governance balancing incentive intensity with coordination needs through intermediate structures like long-term contracts and strategic alliances (em).
2.1 The primacy of asset specificity
Within this framework, asset specificity is universally recognized as the most important dimension. Williamson describes it as TCE’s “big locomotive” and “the most important and most distinctive” dimension (Williamson, 1985). This parameter typically transforms what begins as large-numbers actors competition into bilateral monopoly situations, fundamentally altering governance requirements.
Williamson identifies six specificity types: site, physical asset, human asset, dedicated assets, brand name capital, and temporal specificity. High asset specificity (assets that are almost single context-bouded purpose, not redoployable) creates bilateral dependency and hold-up potential, necessitating safeguarding governance structures that protect relationship-specific investments (jibs).
2.2 Uncertainty
Uncertainty is “the unpredictability surrounding transactions, including environmental changes and behavioral uncertainty” (cf mcgill).
Environmental uncertainty represents the unpredictability surrounding the external business environment. Environmental uncertainty manifests in several forms : market conditions (unpredictability in demand, pricing, and competitive dynamics), technology (inability to forecast technical requirements and technological changes) and volume (difficulty in predicting quantities and demand fluctuations).
“When asset specificity is low, market governance should be preferred whatever the degree of uncertainty, since continuity matters little and new transaction arrangements can easily be arranged by both parties […]When asset specificity is present to a nontrivial degree, however, continuity between the transacting parties becomes important, and adaptive capabilities become necessary”.
Robert J. DAVID and Shin-Kap HAN
A crucial aspect of Williamson’s uncertainty framework is its conditional relationship with asset specificity. High incertainty is costly to market-oriented governance and increase the attractiveness of hierarchical organization governance.
2.3 Frequency
Frequency refers to “the frequency with which transactions recur” and represents how often similar transactions occur between the same parties (jle). The importance of frequency lies in its relationship to the costs of establishing and maintaining a governance structure.
Transaction frequency determines governance structure investment justification, with recurring transactions enabling amortization of specialized governance costs over multiple exchanges. High frequency transactions favor hierarchical governance structure to recover setup costs and develop relationship-specific capabilities (skills, routines, resources).
“Asset-specific transactions that occur frequently require constant monitoring effort in the market, while those that occur only occasionally need not be attended to continuously and do not merit the bureaucratic costs of establishing a hierarchy. […] In the presence of asset specificity, frequency also pushes transactions away from the market and into hierarchy”
Robert J. DAVID and Shin-Kap HAN
2.4 Behavioral assumptions
It’s important to distinguish between the transactional dimensions (the three parameters above) and the behavioral assumptions underlying TCE. The theory rests on two key behavioral assumptions :
- Bounded Rationality – Decision-makers are “intendedly rational, but only limitedly so” (jle)
- Opportunism – “Self-interest seeking with guile” (cf jle)
Bounded rationality reflects cognitive limitations in information processing, storage, and decision-making capabilities, causing all complex contracts to be necessarily incomplete (joie). Organizations must develop adaptive governance mechanisms capable of pre or post adjustment when unforeseen contingencies arise.
Opportunistic behavior involves strategic information manipulation, deception, and calculated efforts to redistribute surpluses through incomplete disclosure (joie). This behavioral assumption drives the need for monitoring mechanisms, performance measurement systems, and enforcement capabilities within governance structures.
It articulates as bounded rationality creates incomplete contracts, opportunism creates the need for safeguards, then asset specificity, uncertainty, and frequency determine which governance structure minimizes transaction costs given the behavioral assumptions. As Simon explained, rational individuals will select a decision that is satisfactory rather than optimal (stanford).
Contemporary research has expanded the bounded rationality assumption beyond simple processing limitations to include interpretation limitations and cognitive biases (amr).
3. Transposition Analysis
The way cybercriminals buy, sell, and organize themselves online shows that they are very good at finding ways to save time, money, and effort (transaction costs) when doing business. They use different types of rules and structures (governance forms, like online forums, private groups, or direct partnerships) to make their illegal activities more efficient and less risky (splunk).
APT41’s dual-mission framework is a good exemple of sophisticated make-or-buy (boundary) decisions, combining state-sponsored espionage with financial cybercrime through contractor-based models. The organization’s arsenal management strategy reveals clear asset specificity considerations: developing custom malware for high-value targets while acquiring cybercriminal commodities for routine operations (googlecloud). Their make-versus-buy decisions validate TCT predictions through systematic choices. High asset specificity activities are internalized: custom malware development for specific targets, supply chain compromise operations requiring deep technical expertise, and specialized infrastructure for sensitive operations. Low asset specificity activities are outsourced: certificate theft rather than developing signing infrastructure, commodity tool acquisition, and standard operational security measures.
Conti’s corporate-style hierarchical structure demonstrates TCT’s explanatory power for criminal organizational evolution. With 80-105 employees across specialized departments, monthly operational costs of $140,000-$165,000, and formal HR processes, Conti achieved organizational efficiency through hierarchical governance addressing high asset specificity requirements (ijcc, flashpoint, deepinstinct). The organization’s custom training programs for Trickbot/Emotet integration represent dedicated human capital investments justifying hierarchical coordination, while purchases from Initial Access Brokers demonstrate market-based decisions for standardized services(cis, checkpoint).
LockBit’s centralized RaaS model displays hybrid governance structures balancing market incentives with coordination requirements. The platform’s 188+ affiliates with 70-80% revenue sharing arrangements create high-powered incentives typical of market governance, while centralized infrastructure and quality assurance programs provide coordination benefits. However, LockBit’s >80% affiliate failure rate demonstrates bounded rationality limitations and information asymmetries inherent in criminal markets (cyr, cisa, globalinitiative).
4. Criminal Modeling
The empirical evidence supports a comprehensive framework applying TCT to cybercriminal organizational analysis through systematic examination of governance structure determinants. This framework integrates Williamson’s four parameters with cybercrime-specific factors to predict organizational boundary decisions and governance form selection.
4.1 Asset specificity assessment
High specificity (hierarchical governance) involves custom malware development, target-specific reconnaissance, specialized infrastructure, relationship-specific expertise, reputation capital. Medium specificity (hybrid governance) will imply semi-customized tools, regional expertise, brand development, and moderate technical specialization. Low specificity (market governance) is intended to commodity tools, standardized access, generic laundering services, basic operational security.
4.2 Transaction frequency patterns
Initial access procurement, credential marketplace transactions, basic tool acquisition are cybercriminal commodities with high transaction frequency, that will fovaor market-oriented solutions. Custom development projects, specialized target campaigns, unique operational requirements are almost unredeployable, displaying a low frequency that invits to hierarchical integration. Cybercriminal partnerships, repeated service relationships, sustained operations are the inbetween, inviting to set up a hybrid structure.
4.3 Bounded rationality manifestations
Criminal organizations exhibit systematic cognitive limitations driving organizational choices. Conti’s deception strategy—telling employees they worked for “ad analytics” companies—demonstrates sophisticated management of bounded rationality to reduce moral hazard and recruitment costs (crimrvix, checkpoint). LockBit’s affiliate failure rate exceeds 80% despite “comprehensive toolkits,” indicating information processing limitations and environmental complexity exceeding individual cognitive capacity (cyr).
4.4 Opportunistic behavior controls
Cybercriminal groups develop sophisticated governance mechanisms addressing hold-up problems. Reputation systems on dark web forums and blackmarkets create switching costs and performance incentives. Escrow services in criminal marketplaces reduce transaction hazards. (kaspersky)
Performance monitoring systems in hierarchical criminal organizations (Conti’s employee reviews, salary structures) align incentives and discourage opportunistic defection.
4.5 Technology’s transaction cost impact
Network infrastructure fundamentally alters transaction cost structures in criminal organizations. Encrypted communications reduce coordination costs enabling global operations, anonymity networks (Tor) decrease detection risks while increasing operational complexity and cryptocurrency integration enables automated payment systems reducing transaction costs while creating new technological dependencies and detection risks. (lawandworld)
5. BreachForums case analysis
When French police arrested five BreachForums administrators (ShinyHunters, Hollow, Noct, Depressed, and IntelBroker) they revealed a sophisticated organization that followed predictable economic patterns (therecord, bleepingcomputer). The administrators were running a business according to the same organizational principles that legitimate companies use.
We have seen that Transaction Cost Theory predicts that organizations will choose their structure influenced by key factors:
- Asset specificity (how specialized their resources are),
- Transaction frequency (how often they do business),
- Bounded rationality (cognitive limitations),
- Opportunistic behavior (people acting in their own self-interest).
The BreachForums case shows these predictions working exactly as expected. The forum’s transition from centralized control to collaborative administration reflects increasing asset specificity and coordination requirements as the platform scaled to 225,000 members (osintteam).
They underwent governance structure changes, from centralized hierarchy under Pompompurin (2022-2023), to hybrid governance under Baphomet and ShinyHunters (2023-2024), to distributed coordination attempts following law enforcement pressure
5.1 Asset specificity drives make-or-buy decisions
They underwent governance structure changes, from centralized hierarchy under Pompompurin (2022-2023), to hybrid governance under Baphomet and ShinyHunters (2023-2024), to distributed coordination attempts following law enforcement pressure (intel471, osintteam).
BreachForums developed highly specialized systems (custom reputation mechanisms, PGP-signed authentication, and proprietary forum infrastructure) while buying standardized services like basic hosting from outside providers. This is a boundary decision based on asset specificity. The administrators’ involvement in “cyber-attacks of a very high degree of technical complexity” shows they kept the most specialized, valuable skills in-house (infosecuritymag).
ShinyHunters’ track record, releasing specialized data from financial services, dating platforms, and major corporations, represents relationship-specific expertise that can’t be bought on the open market (siliconangle). They had to develop these capabilities internally because no external provider could offer them.
5.2 Why some things stay in the market, and others don’t
BreachForums operated as “a marketplace for stolen databases, tools, and access credentials” with high-frequency transactions in standardized products (kelacyber, barracuda). For everyday items like basic hacking tools or common credentials, the platform used market-based trading. But for specialized, high-value assets, they used hierarchical control and quote-like system.
This hybrid governance structure makes perfect economic sense. High-frequency, standardized transactions work best in markets. Low-frequency, specialized transactions need more coordination and control.
5.3 Bounded rationality: When criminal planning pails
Even sophisticated criminal organizations have cognitive limitations. BreachForums v2 went offline in April 2025 after being breached by a MyBB zero-day vulnerability, despite having substantial resources and technical expertise (hackread).
This demonstrates bounded rationality : the idea that people and organizations can’t perfectly plan for every contingency. Users consistently worried about law enforcement honeypots and infiltration after each platform relaunch, showing how uncertainty and incomplete information affected decision-making (osintteam).
These security failures follow predictable patterns that Transaction Cost Theory explains: when environments are complex and uncertain, even smart people make mistakes because they can’t process all the information perfectly.
5.4 Building trust in criminal markets
Criminal organizations face a fundamental problem: how do you trust people who are, by definition, criminals?
BreachForums solved this with sophisticated trust mechanisms : PGP signatures for authentication, reputation systems to track reliability, and rank preservation across platform versions (flashpoint, intel471).
These governance mechanisms address what TCT calls “opportunistic behavior” : the tendency for people to act in their own self-interest, even when it hurts their partners. The careful verification processes during administrator transitions show how much effort went into preventing deception and fraud (“hold-up”) within the organization (osintteam).
5.5 How law enforcement exploits transaction cost vulnerabilities
The French arrests demonstrate something important: international cooperation systematically raises transaction costs for criminal organizations. The coordinated French-US operation shows how multi-jurisdictional enforcement makes criminal operations more expensive and difficult (cyberexpress, therecord).
Arrests across multiple French territories (Paris, Normandy, Réunion) forced the criminal organization to manage complex geographic coordination (infosecuritymag). The US extradition request for Kai West (IntelBroker) adds additional legal and operational complexity.
From a Transaction Cost Theory perspective, this is strategic: make criminal coordination so expensive and difficult that organizations become inefficient or collapse.
5.6 Synthetis
The French arrests of BreachForums operators provide concrete, empirical evidence that Transaction Cost Theory accurately predicts cybercriminal organizational behavior. It is a practical tools for understanding how criminal organizations work and how to disrupt them effectively.
Asset specificity drives make-or-buy decisions. Transaction frequency determines governance structures. Bounded rationality creates exploitable weaknesses. Opportunistic behavior necessitates costly trust mechanisms. And regulatory pressure systematically raises transaction costs.
Understanding these patterns gives cybersecurity professionals and law enforcement concrete strategies for targeting criminal organizations where they’re most vulnerable: their organizational structure and transaction cost management systems.
6. Edge cases
While Transaction Cost Theory (TCT) successfully explains most cybercriminal organizational behavior, some cases break the rules. These limiting cases reveal situations where criminals don’t follow economic logic, showing us the boundaries of what TCT can predict.
6.1 State-Sponsored Cybercrime
State-sponsored cybercrime convergence represents the clearest case where TCT predictions fail. When governments get involved, political objectives override the primacy of economic efficiency.
French ANSSI’s “Threats and Incidents” publications involving espionage activities demonstrates organizational choices driven by strategic rather than transaction cost considerations (anssi). A government-backed hacking group doesn’t care if their organizational structure is economically inefficient if it serves well national security goals.
State-sponsored groups often maintain expensive, redundant capabilities and pursue targets with low financial value but high intelligence worth. A purely economic organization would abandon these inefficiencies, but strategic objectives override cost considerations.
This breaks TCT’s fundamental assumption that organizations optimize for efficiency. When national interests are at stake, efficiency becomes secondary to effectiveness.
6.2 Exit scams
Exit scam behaviors show what happens when opportunistic behavior completely overwhelms governance mechanisms. TCT assumes that reputation systems and repeated interactions will keep people honest because long-term relationships are more valuable than short-term gains. But exit scams prove this assumption wrong.
NoEscape operators’ abandonment of affiliates and LockBitSupp’s reputation damage from non-payment issues demonstrate cases where short-term opportunistic gains exceed long-term relationship value (secureworks).
Criminal operators build up trust and reputation over months or years, then suddenly disappear with everyone’s money. Even though this destroys their long-term earning potential, the immediate payoff is so large that it makes economic sense.
This breaks TCT’s assumption that reputational mechanisms effectively control opportunistic behavior. Sometimes the temptation is just too big, and short-term thinking wins.
6.3 Hacktivism
Ideologically motivated organizations create another puzzle for TCT. These groups prioritize their beliefs over economic efficiency, making organizational choices that seem irrational from a business perspective.
Hacktivist groups exhibit swarm-like organization with weak command structures despite potential efficiency gains from hierarchical coordination. Groups like Anonymous deliberately avoid centralized leadership even though it would make them more effective . Why? Because their ideological commitment to decentralization matters more than operational efficiency. They’d rather be less effective but stay true to their principles than optimize for results. (ijcc)
This reveals a key limitation: TCT assumes economic optimization is the primary goal. But when organizations prioritize values over efficiency, the theory’s predictions break down.
6.4 Post-takedown Panic mode
Rapid organizational dissolution following law enforcement pressure shows what happens when uncertainty becomes so extreme that long-term planning becomes impossible.
Criminal organizations often abandon substantial investments (reputation capital, specialized infrastructure, human capital) the moment law enforcement applies pressure. From a TCT perspective, this seems irrational. Why throw away valuable assets you’ve spent years building?
Extreme uncertainty makes long-term governance structure investments economically irrational. When the probability of organizational survival drops dramatically, it makes sense to cut losses rather than protect investments.
This challenges TCT’s assumption that organizations will adapt their governance structures to changing environments. Sometimes the environment changes so fast and dramatically that adaptation becomes impossible, and abandonment becomes the rational choice.
6.5 The Jurisdiction cat and mouse game
Cross-jurisdictional complexity creates environments where traditional governance mechanisms simply don’t work. International law enforcement coordination difficulties enable what we might call “organizational arbitrage strategies” : criminal groups that exploit the gaps between different legal systems.
These situations create environments where traditional governance structures provide insufficient protection against opportunistic behavior by state actors or competing criminal organizations. When you’re operating across multiple jurisdictions with different laws, enforcement capabilities, and cooperation levels, normal trust and reputation mechanisms break down.
For example, a criminal organization might have solid reputation and trust relationships working in one jurisdiction, but face completely different rules and risks in another. The governance mechanisms that work domestically fail internationally.
6.6 Practical implications
Understanding these limitations is crucial for cybersecurity professionals and law enforcement because it helps identify when normal economic logic doesn’t apply.
- For threat intelligence analysts: Don’t expect state-sponsored groups or ideologically motivated actors to follow normal business logic. Their organizational choices serve different purposes.
- For law enforcement: Exit scam vulnerabilities represent windows of opportunity when normal trust relationships break down. Jurisdictional complexity can be exploited, but it also creates enforcement challenges.
- For defensive planning: Organizations facing ideologically motivated attackers or state-sponsored threats need different defensive strategies because these attackers don’t follow normal cost-benefit calculations.
Transaction Cost Theory is a powerful tool for understanding cybercriminal organizations, but it’s not universal. Political objectives, extreme uncertainty, ideology, and jurisdictional complexity can all override economic logic.
But recognizing these limitations makes TCT even more useful by helping us understand when to apply it and when to look for other explanations. The most sophisticated cybercriminal threats often involve exactly these limiting cases, which is why understanding the boundaries of economic logic is as important as understanding the logic itself.
7 . Use Transaction Cost Theory for Cybersecurity Defense
Transaction Cost Theory helps us understand cybercriminal organizations and gives us concrete strategies for disrupting them. Here’s how cybersecurity professionals and law enforcement can use these insights practically.
7.1 Target What They Can’t Replace
Asset specificity-based disruption strategies focus on attacking the things criminal organizations have invested heavily in and can’t easily replace. If you want to hurt a business, you don’t target the things they can buy anywhere, you target their unique specialized assets.
Criminal organizations make the same kinds of investments that legitimate businesses do. Some investments are relationship-specific: they only work within that particular organization or partnership. These are the most valuable targets because criminals can’t simply buy replacements on the open market.
7.2 The Disruption Priority Matrix
This matrix helps prioritize defensive efforts based on how much impact you can achieve. Remember, this isn’t a rigid checklist but a guide that should be adapted to specific situations and available resources.
High Priority Targets (High Asset Specificity)
These represent investments that criminal organizations can’t easily replace:
- Custom malware development capabilities requiring specialized skills: Disrupting the teams and knowledge that create malware. When you target the human expertise and development processes, criminals can’t simply download a replacement.
- Relationship-specific infrastructure investments (C2 servers, specialized hosting): Criminal groups often build custom command-and-control infrastructure tailored to their specific operations. Unlike generic hosting, these systems are designed for particular malware families or operational approaches, making them irreplaceable.
- Reputation capital in elite criminal forums: Criminal organizations invest years building trust and status in exclusive forums. This reputation can’t be quickly rebuilt and is essential for high-value partnerships and transactions.
- Human capital with organization-specific knowledge: Key personnel who understand the organization’s unique processes, relationships, and technical systems. When these individuals are removed, the knowledge goes with them.
- Brand name capital in criminal service markets: Established criminal “brands” like major ransomware groups have built recognition and trust that new entrants can’t easily replicate.
Medium Priority Targets (Hybrid Governance)
These targets balance customization with flexibility, making them moderately difficult to replace:
- Service provider relationships in criminal markets: While not completely unique, established relationships with reliable service providers (money launderers, hosting services, etc.) take time and effort to develop.
- Regional operational expertise and local partnerships: Knowledge about specific geographic markets, local law enforcement patterns, and regional business practices has value but can potentially be rebuilt.
- Specialized tool development with multiple applications: Tools that are customized but have broader utility across different operations. More valuable than commodity tools but less critical than completely bespoke solutions.
- Cross-border coordination mechanisms: Systems for managing international operations. Complex to establish but not impossible to recreate.
Lower Priority Targets (Market-Based)
These are standardized services that can be easily replaced:
- Commodity tool marketplaces with multiple suppliers: Generic hacking tools available from multiple sources. Disrupting one marketplace just sends customers to competitors.
- Standardized service providers (hosting, communications): Basic services available from many providers. Criminal organizations can quickly find alternatives.
- Generic cryptocurrency laundering services: While disruptive, these services are offered by multiple providers and can be substituted relatively easily.
- Basic operational security measures: Standard security practices that don’t require specialized knowledge or relationships.
7.3 Four Ways to Disrupt Criminal Efficiency
These are flexible approaches for making criminal operations more expensive and difficult. The goal is to force criminal organizations into less efficient structures or abandon operations entirely.
Increase Coordination Costs
The strategy here is to make it harder and more expensive for criminals to work together. Target communication infrastructure, encrypted messaging platforms, and coordination mechanisms to raise organizational overhead and force less efficient governance structures.
This doesn’t mean you need to break every communication channel. Instead, focus on making coordination so costly and uncertain that criminal groups struggle to maintain effective teamwork. When coordination becomes expensive enough, organizations either become inefficient or fragment.
Exploit Bounded Rationality
Criminal organizations have cognitive limitations just like legitimate businesses. Introduce information asymmetries through deception operations, technical complexity increases, and rapid defensive adaptations that exceed criminal organizations’ cognitive processing capabilities.
The idea is to overwhelm their decision-making capacity. When the environment (the criminal one or the target’s one) becomes too complex to understand and adapt to quickly, even smart criminals make mistakes. This strategy leverages the fact that human cognitive capacity is limited, regardless of criminal intent.
Amplify Opportunistic Behavior
Disrupt reputation systems, introduce uncertainty about partner reliability, and create conditions where short-term opportunistic behavior becomes more attractive than long-term cooperation.
Criminal organizations rely on trust and reputation to function. When you can make criminals doubt each other’s reliability, you encourage the kind of short-term thinking that destroys long-term partnerships. Think of it as encouraging criminal organizations to self-destruct through internal mistrust.
Frequency Disruption
Interrupt high-frequency transactions (credential marketplaces, access brokers) to force criminal organizations toward less efficient governance structures and increase per-transaction costs.
Many criminal operations depend on high-volume, routine transactions. By disrupting these regular business flows, you force criminals to use more expensive, less efficient methods for conducting business.
7.4 Organizational Intelligence Collection: What to Watch For
To setup an organizational intelligence capability, focus intelligence collection on governance structure indicators in addition to technical indicators. Look for:
- Decision-making processes: How do criminal organizations make strategic choices? Who has authority? How do they resolve disputes?
- Resource allocation patterns: Where do they invest their time, money, and expertise? What do they prioritize?
- Boundary management strategies: What do they do in-house versus outsource? How do they manage partnerships?
- Adaptation mechanisms: How do they respond to pressure or changes in their environment?
Monitor organizational responses to operational pressure to identify asset specificity patterns and governance structure vulnerabilities. The goal is understanding the organization as a business system, not as a technological threat.
7 . Conclusion
Transaction Cost Theory proves to be a powerful tool for understanding how cybercriminal organizations actually work. From individual hackers to sophisticated Crime-as-a-Service platforms, the evidence shows that criminals follow predictable economic patterns when building their organizations.
Asset specificity consistently drives make-versus-buy decisions across all types of criminal organizations. When criminals need something highly specialized and valuable, they build it in-house. When they need something standardized, they buy it from criminal markets. This pattern holds whether we’re looking at solo operators or major ransomware groups.
Governance form selection follows predictable patterns based on three key factors: how often transactions happen, how uncertain the environment is, and how much they need to control opportunistic behavior. Criminal organizations aren’t randomly structured but organized according to economic principles that minimize their transaction costs.
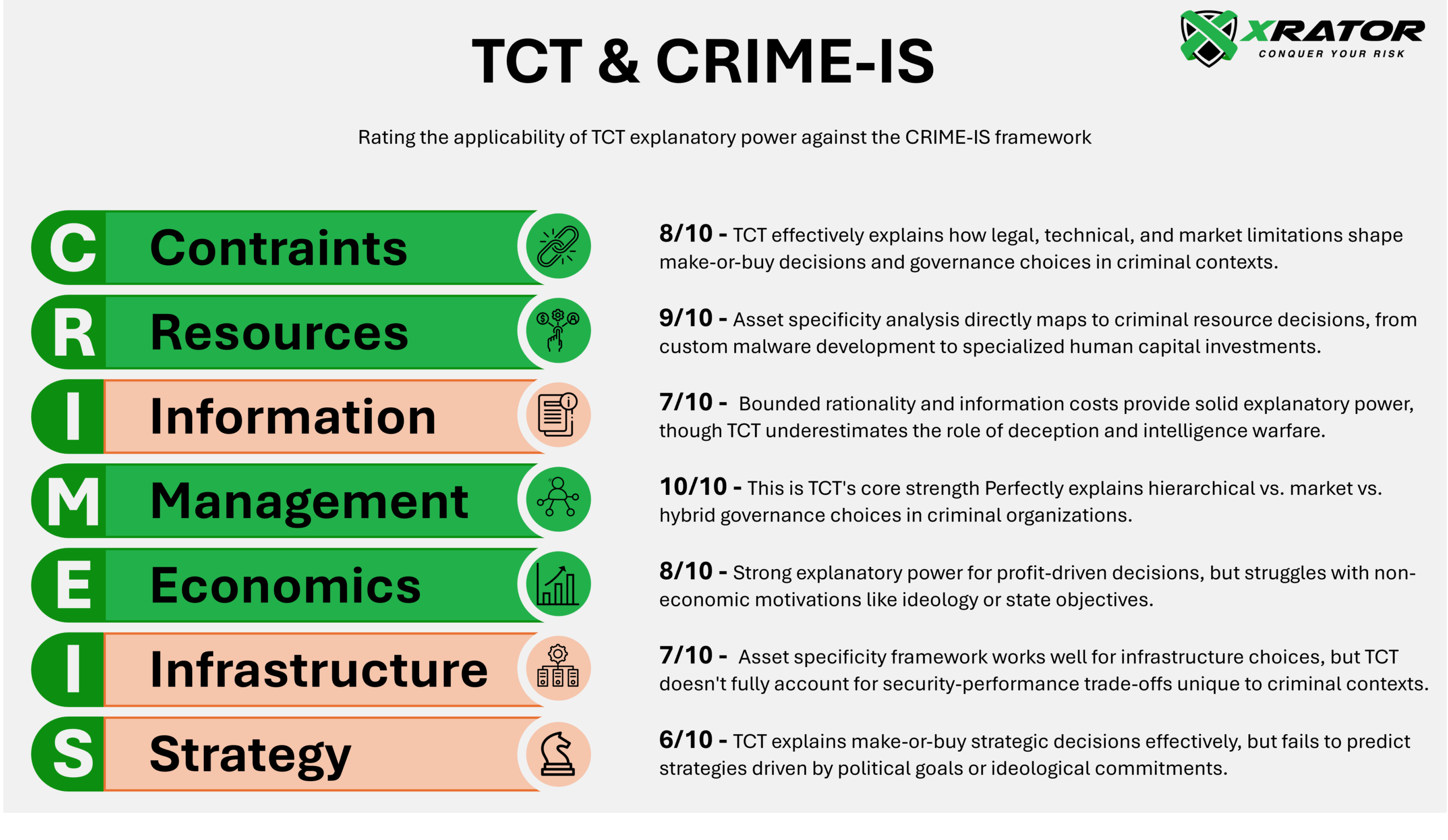
The framework’s practical applications extend beyond explaination to concrete defensive strategies. By systematically analyzing criminal organizational structures through TCT lenses, cybersecurity practitioners can identify high-impact disruption targets, predict organizational adaptations, and design efficient intervention strategies that exploit transaction cost vulnerabilities.
However, limiting cases reveal framework boundaries in extreme uncertainty environments, ideologically motivated organizations, and state-sponsored operations where non-economic objectives override efficiency considerations.
| Threat Taxonomy | Cybercrime | APT | Explanation |
| Level 1 Individual actors | 8/10 | 4/10 | Individual cybercriminals follow economic logic well; individual state assets operate under political directives |
| Level 2 Small groups | 8/10 | 5/10 | Criminal groups optimize for efficiency; small APT teams balance mission requirements with resource constraints |
| Level 3 Formal org. | 7/10 | 3/10 | Criminal enterprises follow business logic; formal APT groups prioritize strategic objectives over efficiency |
| Level 4 Ecosystems | 6/10 | 2/10 | Criminal ecosystems balance economic and strategic factors; multi-APT coordination serves primarily political goals |
| Level 5 Service platforms | 7/10 | 1/10 | CaaS platforms optimize for market efficiency; state cyber warfare infrastructure serves national security imperatives |
The analysis reveals a significant divergence between cybercrime and APT applicability of Transaction Cost Theory. Cybercriminal organizations consistently demonstrate economic optimization behavior, with TCT explanatory power remaining strong across all organizational levels despite some decline at higher complexity levels.
APT groups, conversely, show systematic deviation from economic logic as organizational sophistication increases. While individual contractors and small teams may follow efficiency principles, formal state-sponsored operations increasingly prioritize strategic objectives over transaction cost minimization. This divergence suggests that organizational motivation fundamentally determines TCT applicability – profit-driven entities follow economic logic regardless of scale, while politically-motivated entities abandon efficiency optimization as they become more formally integrated into state structures.
The five-level taxonomy proves highly relevant precisely because it captures this motivation-structure interaction. The taxonomy effectively distinguishes between economic and political organizational drivers, making it a valuable analytical tool for predicting when TCT will provide explanatory power versus when alternative frameworks (political science, military organization theory) become necessary.
Conti’s hierarchical governance was optimal for high asset specificity operations requiring extensive coordination, while LockBit’s platform model was superior for low asset specificity operations emphasizing scalability and resilience. Conti’s hierarchy enabled sophisticated operations and high revenue generation but created single points of failure that proved fatal under pressure.
The Transaction Cost Theory framework demonstrates that even illegal organizations follow predictable economic logic in their governance choices, with asset specificity, transaction frequency, and environmental uncertainty serving as key determinants of organizational structure.
Our next article will examines Henry Chesbrough’s Open Innovation Paradigm.