The corporate habits shift toward hybrid or remote work became obvious and widespread with the COVID-19 crisis. But what was an emergency response to the global economy disruption is here to stay. Remote work aggravate existing weakness in organization’s networks while coping with a steadily rise of cyber threats. With laptop and computer out of the corporate shelter, they became a particularly interesting target for cybercriminal.
According to Vedere Labs, about 63% of all devices affected by a vulnerability are computer with a 9/10 average CVSS score.
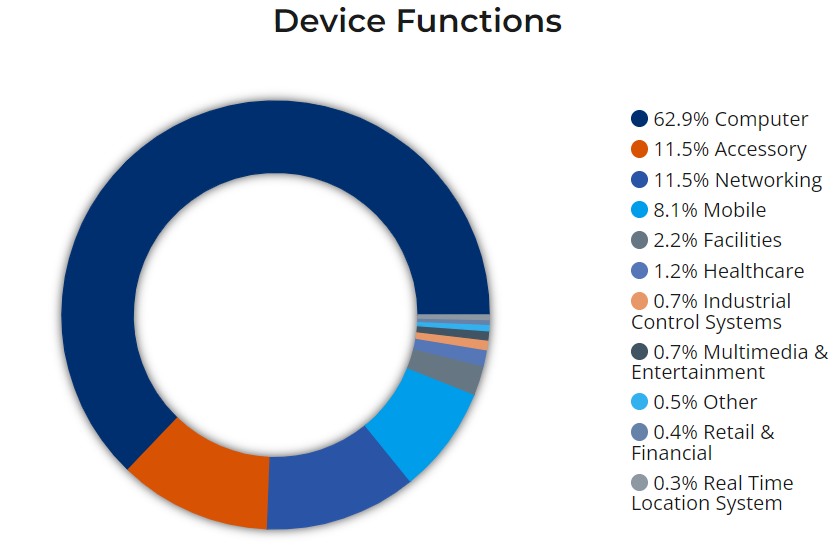
Endpoint and Supply chain are organization weakspot
In this context of increasing pressure on endpoint, Unified Extensible Firmware Interface (UEFI) attacks are rising. As a low-level firmware, it allows attacker to achieve greater persistence and defense evasion to install their malware. Furthermore, digital transformations and industry 4.0 are adding millions of new devices to the potential attack surface.
In addition to the endpoint pressure, organizations are also hit in another vulnerable area: software supply chain attack. Enterprises depend on software stacks to gain access to other components in their software stacks, and those stacks are vulnerable to supply chain attacks, such as the SolarWinds or the Kaseya attacks.
A multilayer approach to security, which protects hardware and software at every level, can be quite effective at countering these threats and others in the future. Because an layered approach is not dependent on any one component for security, it can go a long way in countering these threats and others.
Adding hardware layer of security
A device’s layers of software and hardware can be safeguarded using multilayered security. In addition to safeguarding devices against outside network, service, and software threats, multilayered security helps safeguard against attacks that originate from the outside. This approach is particularly effective for protecting the devices employees use outside of the office.
Hardware multi-layered security offers three main benefits to protect user information and identities:
- Preventing threats from compromising the operating system by securing it below the operating system level with dedicated security hardware.
- Combating attacks that bypass software security by using hardware encryption.
- Preventing malicious actors from exploiting security holes between hardware and software by integrating hardware and software.
- Manage memory manipulation at the hardware level to prevent memory attacks such as buffer overflow.
Hardware and software vendors must work closely together to provide the coordination necessary for robust, multi-layered security. AMD and Microsoft are an example of this coordination, and they work together to provide the best hardware and software solutions to customers.
How Hardware and software vendors collaborate for cybersecurity
Working together, AMD and Microsoft have integrated hardware and software security features to protect any kind of endpoint.
The Pluton chip-to-cloud security technology created by Microsoft is used on Windows 11 PCs to protect user identities, data and applications. The Pluton chip is the silicon-based hardware root of trust for the Windows ecosystem. Microsoft’s Pluton chip works in concert with the AMD Ryzen PRO 6000 Series processor’s. Or with AMD Secure Processor (ASP), a dedicated security coprocessor, to protect user identities and data. In addition to protecting system integrity by authenticating the firm’s initial firmware, it also increases system integrity by authenticating the initial firmware loaded on PCs.
AMD Shadow Stack control flow protection thwarts malware that attempts to redirect the steps taken by legitimate software. This hardware-based protection detects anomalies by comparing stack or subroutine sequence information with a copy stored in hardware.
AMD Ryzen PRO processors let you encrypt the entire system memory, providing more comprehensive protection than application-level encryption. Each time the computer boots up, a unique key creates to encrypt the memory, preventing attackers from accessing passwords and other sensitive information stored in memory, even if they gain physical access to the system.


