Even if cybersecurity is more and more discussed among organization top executives, CISO still struggle to push their agenda. Common problem are the knowledge and understanding gap between chief cybersecurity expert and the C-suite. Storytelling is a very powerful communication techniques that is mastered by marketing and influencers. CISO should embrace this techniques as their role is now less technical and more about convincing and building strong relationship inside the organization they protect.
Cybersecurity Storytelling
humans have always been innately capable of learning through storytelling, and it remains one of the most effective forms of communication. Corporate life frequently overwhelm our natural instincts with data and analysis. Our job as security leaders, however, is increasingly about producing and strengthening relationships.
To tell a tale well is an excellent way to accomplish several positive outcomes. As a result, listeners are able to recollect more details and facts, and they listen longer and more attentively. A tale can be used to dress up boring messages in an eye-catching package. It slows down thinking and establishes credibility and trust, and it can establish emotional bonds that draw people in and inspire positive thoughts and choices.
Cybersecurity tales connect problems, asks, and positive outcomes.
Turn your rationale to an emotional journey
Make certain that the audience, whether interns or board members, understands that this tale relates to them and is worthy of their attention. To do so, many narrative presentations begin with an audience interaction, such as ‘How many of you X ?’. By immediately establishing a collective concord on a crucial aspect of the story, you establish a strong foundation for your scenario.
Since decisions are based on emotions, which are inspired by tales, we should appeal to the audience’s emotions. The hero’s journey, or monomyth theory, is one option, but a down-on-his-luck character will similarly draw sympathy. Despite their seniority, listeners will be more drawn to a human narrative than a corporate one, so create characters who are relatable. The narrative structure is the same that any writer or scenarist will use in entertainment production:
- The status quo: you depict the normal life and the context or your narrative world.
- The catalyst: trouble arise and a disruptive event put your story in motion and push your persona to got out the comfort zone.
- The rising action: the hero jump for trouble to solution, keeping some mystery to build the momentum.
- Down the rabbit hole: everything seems out of control, unsolvable, the complete chaos with no shinny horizon.
- The resolution: The persona solved the problem, and the initial status quo comes back but better, improved.
- Lesson learned: just like at the end of children tales, key lessons are made explicit to strike your point.
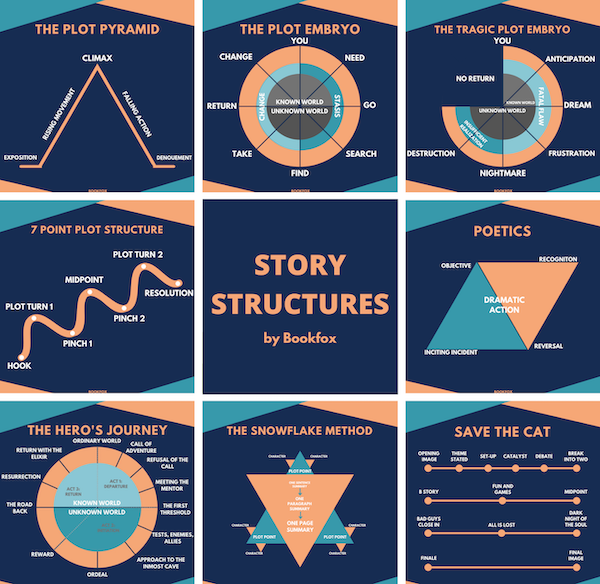
Comparison of narrative structure for cybersecurity storytelling (source).
What you want to do is describe the world as it is today in addition to how it might be, using pictures to support your point. Tie this to the characters in your story to make it seem real and relatable. It is important to emphasize how your solution will create a positive change in the world by making it clear.
The tale should portray how your solution is logical, how it addresses and combats the issues you’ve raised, and how it will result in a positive ending.
Proper time to use a cybersecurity story
CISO don’t always have a lot of time to express their point. They may also suffer from stereotype, someone that is doing virtual stuff only bound to boring automata logic. Hence, using a story is not always what is expected, and it is not a silver-bullet. You have to use it in proper time and accurate situation
Awareness, best practices and cultural change
The perfect momentum to use cybersecurity storytelling is when the CISO is facing the monstrous human factor. When you tell a story about danger and cyber-consequences, and then offer an alternative path, you can create a dominating learning opportunity—especially when you corroborate that tale with real-life examples.
People will unconsciously copy characters they can relate to. Used during awareness session, pay attention to build a story that your audience can relate with and a character that represent them.
Transmit complex situation to the senior management
According to cognitive psychologist Jerome Bruner, a fact is 22 times more likely to be remembered if it is wrapped in a story. When explaining complex problem or situation to the board or to top executives, the storytelling will make it more easy digest and remember. Using cherrypicked analogies and metaphor, you can close the knowledge gap. More importantly, you make it rememberable and explainable for your audience that will be able to assimilate and propagate your story.
Weighting on strategic decision
The purpose of employing narrative as a hook to influence business decisions is to ensure that employees across all levels of seniority can remember and relate to the rationale for change. Safeguard an initiative from diversion or defunding. Tell a story in your top-level presentation. Then describe it as a summary of why you made the decision and what it is.
If your point is memorable, you will gain supporter that will propagate your point to other stakeholder. From a cost-center manager, you will turn your role to a key pillar for any strategic decision.
Build your leadership
Leadership is about accessibility, trust and credibility. You can turn into someone that is able to explain to anyone very complex situation. To be the mirror any executive needs to reflect and take smart decision. This will build your relationship network inside and across the organization.
Awesome cybersecurity leaders concentrate on protecting and enabling enterprise priorities. Not securing computer. In order to be effective in their increasingly multifaceted role, they must have a range of capabilities and competencies. Storytelling and influence is definitely one of them.


