In the high-stakes game of cybersecurity, innovation becomes the key to survival. For those safeguarding systems against malicious attacks, the value of a robust defense cannot be overstated. It’s within this space that a groundbreaking tool like RatChatPT can make a significant difference, its unique features making it a top-tier choice for those working in offensive security and red team operations.
RatChatPT represents an exciting fusion of artificial intelligence (AI) and offensive security. Developped by XRATOR and Spartan Conseil, it’s a tool that amplifies the effectiveness of red team operations, providing a stealthier, more efficient avenue for security experts to assess their defensive systems. This includes a vast range of security systems, from endpoint detection and response (EDR) solutions to data loss prevention (DLP) systems, firewalls, and beyond.
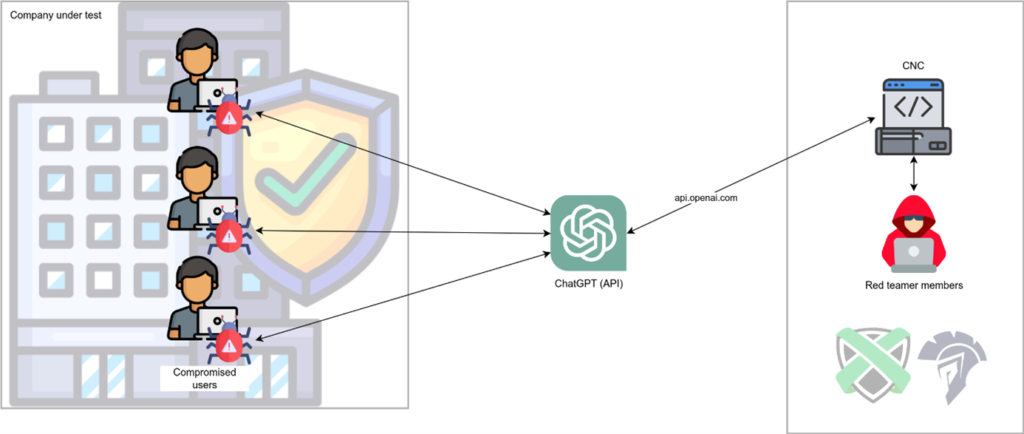 This AI-driven solution allows for a level of automation previously unimaginable in the field of cybersecurity. RatChatPT aims to revolutionize the red teaming landscape, leveraging the capabilities of OpenAI’s ChatGPT API for a novel application. It’s a testament to the potential of AI and how it can be harnessed in a proactive and ethical manner for better network protection.
This AI-driven solution allows for a level of automation previously unimaginable in the field of cybersecurity. RatChatPT aims to revolutionize the red teaming landscape, leveraging the capabilities of OpenAI’s ChatGPT API for a novel application. It’s a testament to the potential of AI and how it can be harnessed in a proactive and ethical manner for better network protection.
Understanding RatChatPT: Navigating the Landscape of AI-driven Penetration Testing
Harnessing AI for Cybersecurity
The genesis of RatChatPT reflects a paradigm shift in how AI is employed within the realm of cybersecurity. The burgeoning growth of AI technology is unarguably shaping numerous industries, and cybersecurity is no exception. RatChatPT, inspired by project like GC2-sheet (using Google as proxy) or DropboxC2C (using Dropbox as proxy), aims to maximize this AI potential, automating the traditionally manual tasks of security experts. The result is an enhanced, more efficient penetration testing operation that remains one step ahead in the security landscape.
Functionality of RatChatPT
RatChatPT isn’t just another tool in the cybersecurity arsenal; it’s a game-changer. The way it functions makes it unique among its counterparts. Rather than necessitating custom domain or VPS setup for communication, it utilizes the OpenAI API as a communication proxy. The innovative system comprises two elements: the implants (termed ‘Agents’) and a command & control mechanism (referred to as the ‘Handler’), both communicating through the OpenAI API domain.
As OpenAI Files interactions with the “Files” endpoint are free of charge, RatChatPT requieres no money to be spent.
 Leveraging Go for Cross-Compilation and Portability
Leveraging Go for Cross-Compilation and Portability
RatChatPT was developed using the Go programming language, a decision underpinned by the language’s portability and cross-compilation capabilities. These features are integral to the functioning of the Agents in RatChatPT’s architecture. Moreover, the Go language extends the knowledge base of developers involved in the project, encouraging a symbiosis of learning and development.
Exploring the Technological Core of RatChatPT
System Architecture
At the core of RatChatPT’s functionality are the API calls to the OpenAI system, facilitating file upload, listing, download, and deletion.
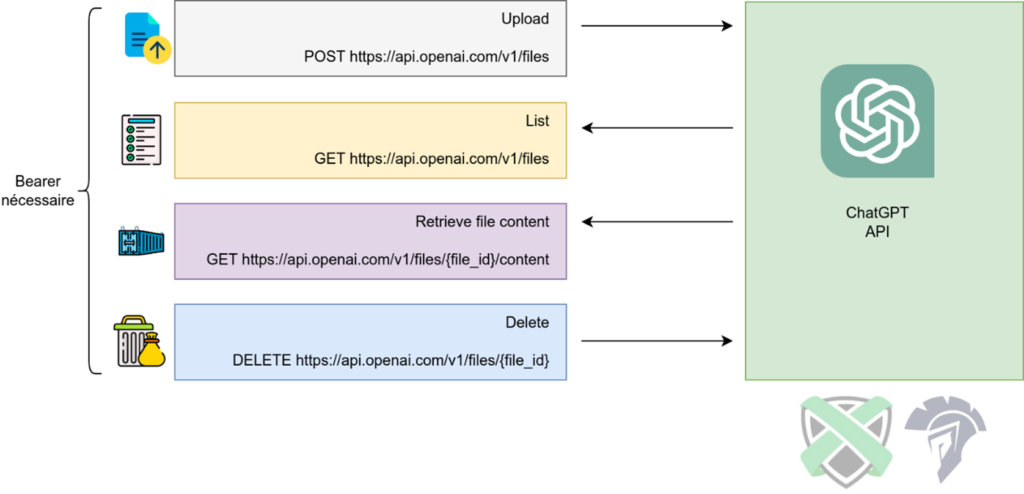 These calls enable two primary actions: the onboarding of a new agent and the execution of arbitrary commands with feedback. The first step being once the agent is executed on the targeted host to register itself on the Handler by pushing its onboarding file on openai Web site.
These calls enable two primary actions: the onboarding of a new agent and the execution of arbitrary commands with feedback. The first step being once the agent is executed on the targeted host to register itself on the Handler by pushing its onboarding file on openai Web site.
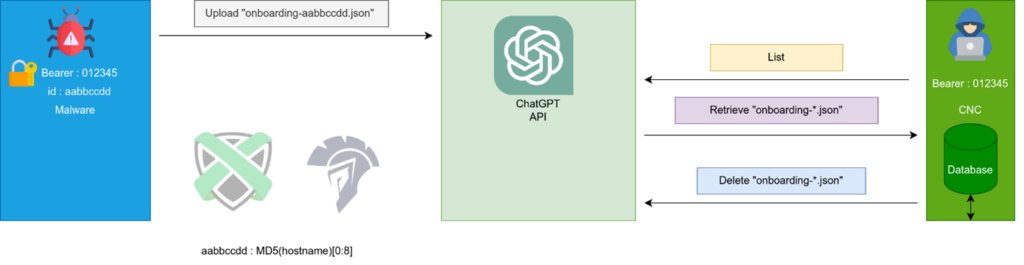
Once onboarded, in the Handler Web interface it is possible to upload obfuscated files containing orders for a specific Agent. This Agent will then retrieve those files periodically, then decrypt the order, execute it and upload the obfuscated answer on the openai Web site as well as delete the order file.
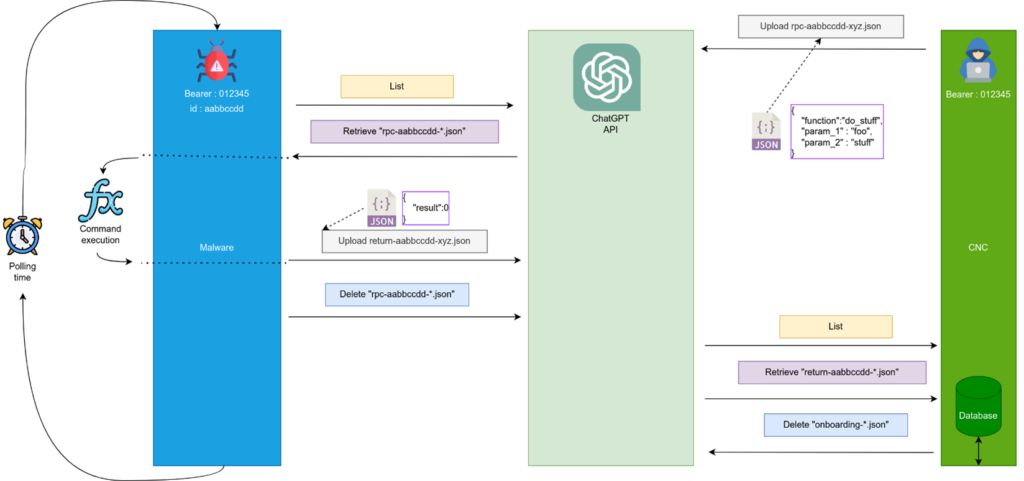
By harnessing the OpenAI API, RatChatPT takes a significant step towards revolutionizing how red team operations are conducted.
Technological Choices
RatChatPT’s agent has been successfully tested on various operating systems, including Windows 10, 11, and different Linux distributions such as Ubuntu 22.04, Debian 11 and Arch Linux.
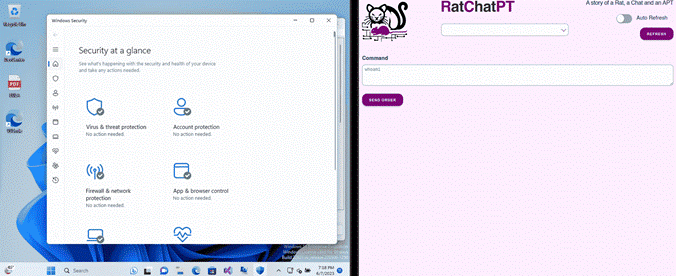 The HTML/CSS/JS Handler interface is compatible with any browser, making it usable by multiple operators simultaneously. These choices highlight the tool’s adaptability and cross-platform effectiveness.
The HTML/CSS/JS Handler interface is compatible with any browser, making it usable by multiple operators simultaneously. These choices highlight the tool’s adaptability and cross-platform effectiveness.
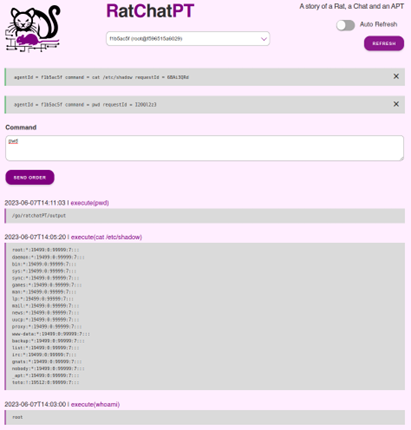 Stealth and Detection
Stealth and Detection
When it comes to offensive security tools, the quieter, the better. The stealth of RatChatPT, as verified by Virus Total, is noteworthy. Despite no customization, only a minor fraction of the tested antivirus programs flagged RatChatPT as malicious, underlining its stealthy nature.
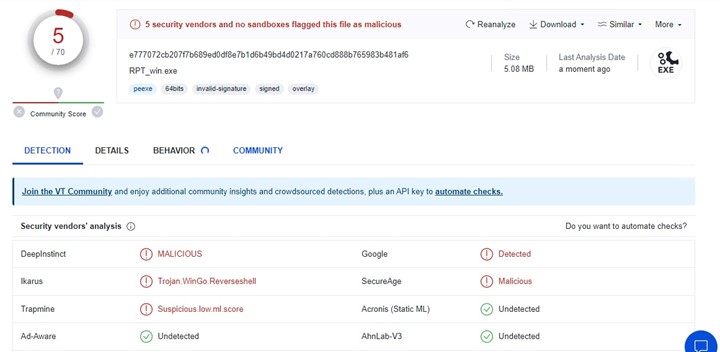 With more advanced obfuscation techniques, the result could be close to zero.
With more advanced obfuscation techniques, the result could be close to zero.
Looking Ahead: The Future of RatChatPT and its Countermeasures
What’s Next for RatChatPT
There’s considerable room for expansion and further development within the RatChatPT framework. Possible future features could include capabilities like keyboard monitoring, screen capture, file management, network access, and web browser control, all potentially giving red teams a significant edge in their operations.
A Robust Defense: Mitigating Risks from RatChatPT
Although RatChatPT can bypass some network-based defense systems, a multi-layered defense strategy can counteract its effects. A well-configured EDR should be able to trigger alerts based on the agent’s activities. Additionally, training users on digital hygiene practices can provide an added layer of security.
Evaluating Security: Why Testing Matters
If you have concerns about your network’s security, the answer lies in testing your defenses. Red teaming exercises, such as those offered by XRATOR, can help expose vulnerabilities before they’re exploited by malicious actors. These exercises equip organizations to respond proactively to potential cyber threats.
Conclusion
The advent of AI has opened up new avenues of possibility in many fields, and cybersecurity is among the most prominent. RatChatPT stands as a testament to this innovation, harnessing the power of AI to revolutionize offensive security and red teaming operations.
Its unique features, such as the usage of OpenAI API as a proxy for communication, the adaptability of the Go language, and its inherent stealth, make it a powerful tool for cybersecurity professionals. Moreover, its potential for further development promises an exciting future for AI in the world of cybersecurity.
However, it’s crucial to remember that tools like RatChatPT should be used responsibly. With this technology comes an increased responsibility to conduct activities within legal boundaries. Cybersecurity is not just about offensive operations; it’s also about building robust defenses and fostering a culture of digital hygiene.
RatChatPT represents the next step in the evolution of cybersecurity, providing a glimpse of what the future holds. As we move forward, it’s essential to keep an eye on such advancements while strengthening our defenses accordingly. It’s this dual approach that will ensure we stay one step ahead in the ever-evolving cybersecurity landscape.
The Github Project is hosted on our Partner’s Github : https://github.com/spartan-conseil/ratchatpt



