This article is part of the Criminal Information System Management series, cybercriminal strategic positionning section.
Key Takeaways
- Kim & Mauborgne’s Blue Ocean Strategy directly predicted Revil’s and Conti’s market entry approach.
- Cybercriminals preserve institutional knowledge, transfer capabilities across organizational boundaries, and maintain competitive advantages through planned organizational death and rebirth.
- We focus on Indicators of Compromise while criminals focus on Indicators of Opportunity. Defensive strategies targeting technical capabilities miss the strategic capabilities that enable criminal’s continuous adaptation and innovation.
- Counterintuitively, unlimited state resources make APT groups strategically lazy. Without market pressure, resource constraints, or competitive dynamics, state-sponsored actors develop fewer strategic capabilities than profit-driven criminals.
- Criminal platforms demonstrate understanding of network effects, platform dynamics, and ecosystem management than most legitimate tech companies. Their affiliate programs, revenue sharing models, and customer support often exceed legitimate SaaS quality standards.
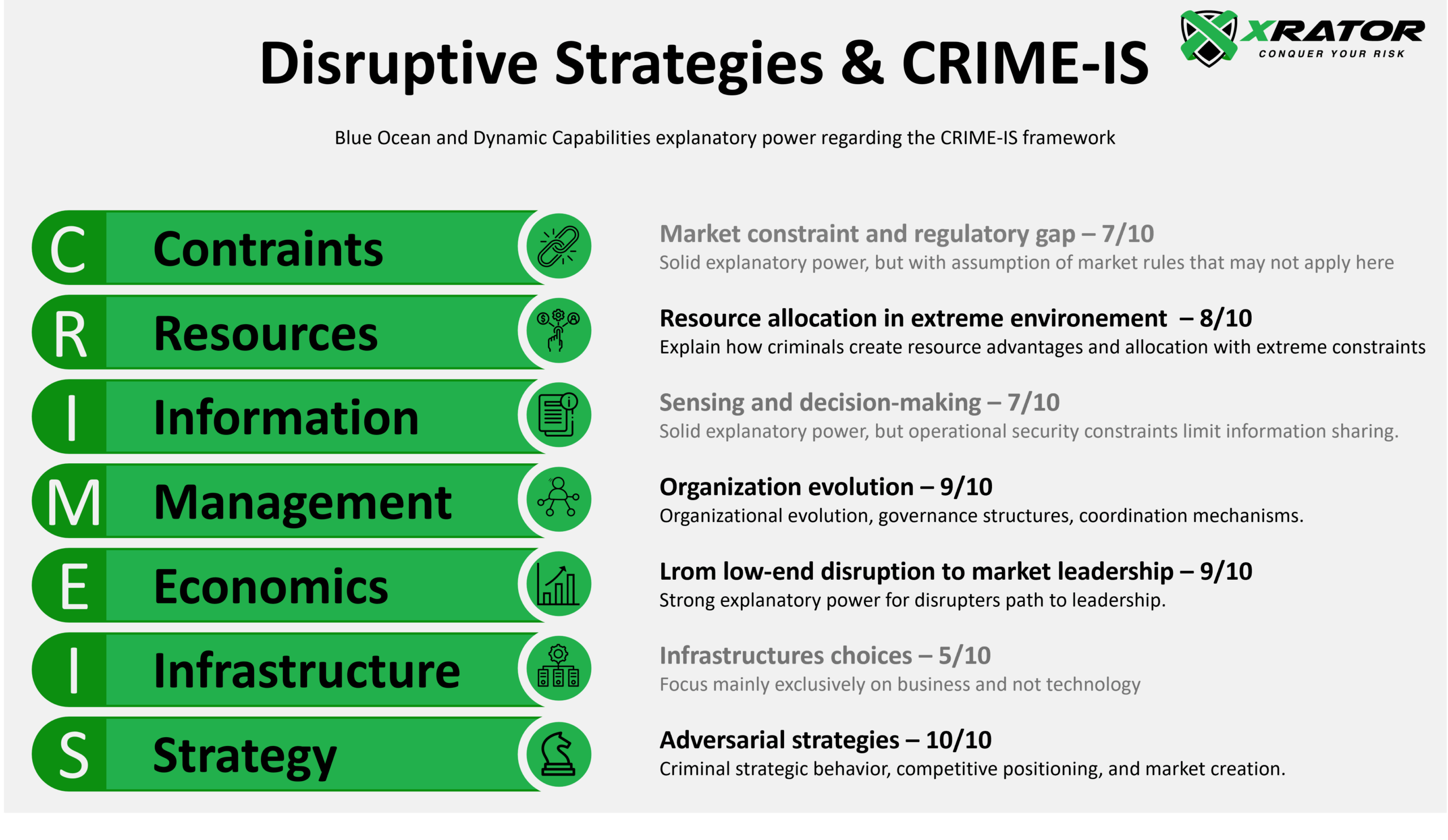
1. Introduction
The intersection of cybercrime and strategic management represents one of the most understudied yet critical domains in contemporary organizational research. As cybercriminal organizations is regularly reported to generate approximately $1.5+ trillion range annually (informationage, secureworks) heir sophisticated operational structures demand theoretical frameworks beyond traditional criminological approaches (whitehouse, sensors).
Chief Information Security Officers (CISOs) and Cyber Threat Intelligence (CTI) analysts increasingly confront adversaries operating with business-like strategic frameworks, demonstrated by the 30% year-over-year rise in active ransomware groups (secureworks2) and the emergence of corporate-style Ransomware-as-a-Service operations generating $180 million annually (sensors, coveware).
Yet significant theoretical questions remain unresolved. Can Kim and Mauborgne’s Blue Ocean Strategy framework meaningfully apply to illegal market creation? Do Christensen’s disruptive innovation patterns manifest in criminal contexts? How do Teece’s dynamic capabilities relate to criminal organizational adaptation under extreme regulatory pressure?
This research provides theoretical analysis and empirical validation to answer these foundational questions.
2. Theoretical Synthesis
The convergence of three foundational business strategy frameworks (Blue Ocean Strategy’s four actions framework, Christensen’s disruptive innovation theory, and Teece’s business model innovation model) reveals a unified theoretical architecture for understanding market creation and organizational adaptation. This convergence represents the theoretical zeitgeist of the 2000s emphasizing disruptive innovation and business model innovation (rtm, jsit).
Blue Ocean Strategy’s Eliminate-Reduce-Raise-Create (ERRC) framework provides the operational mechanism for value innovation through strategic reconstruction of competitive factors (joecotellese, socialsciences). The theoretical foundation rests on simultaneous pursuit of differentiation and low cost to create uncontested market space. A concept that maps directly onto criminal organizations’ systematic exploitation of regulatory gaps and market inefficiencies.
2.1 Blue Ocean’s 6 Paths Frameworks and its relationship with Blue Ocean’s 4 Actions
Blue Ocean Strategy’s analytical architecture combines two complementary frameworks serving distinct strategic functions in market creation (hbr).
The 6 Paths Framework provides systematic methodology for identifying blue ocean opportunities by reconstructing industry boundaries across:
- Alternatives: Examine other industries serving the same fundamental customer need through different approaches.
- Strategic groups: Analyze different strategic positioning within the same industry (luxury vs budget segments).
- Buyer gains: Map the complete purchasing chain from influencers to users to purchasers.
- Complementary offerings: Explore products and services used before, during, and after your solution.
- Functional/Emotional orientation: Shift between rational utility focus and emotional experience emphasis.
- Temporal dimensions: Identify emerging trends and shifts that will reshape market boundaries over time.
This framework acts as the scanning mechanism, mapping potential market characteristics for reconstruction.
The 4 Actions Framework (Eliminate-Reduce-Raise-Create) serves as the operational execution tool, providing concrete mechanisms for implementing value innovation once opportunities are identified. The ERRC grid transforms strategic insights into specific value proposition modifications that simultaneously pursue differentiation and cost reduction.
The relationship between these frameworks is both sequential and integrated, creating a systematic approach to market creation rather than opportunistic innovation:
- Organizations first apply 6 Paths analysis to identify promising boundary reconstruction opportunities within their competitive landscape,
- Then deploy the 4 Actions framework to redesign value propositions within that identified opportunity space.
This sequential logic prevents random innovation attempts by grounding the 4 Actions implementation in systematic market analysis. The integration ensures that value innovation efforts target genuine market opportunities rather than arbitrary competitive factors.
2.2 Teece’s Dynamic Capabilities and criminal adaptation
Teece’s (2010) framework emphasizes that business models “articulate the logic that demonstrates how a business creates and delivers value to customers [and] outlines the architecture of revenues, costs, and profits” (lrp). Criminal organizations demonstrate sophisticated dynamic capabilities through systematic sensing, seizing, and transforming mechanisms (fip, sr). The Conti ransomware group’s leaked communications reveal explicit strategic planning processes, including market analysis, competitive positioning, and performance management systems that directly parallel Teece’s capability framework (krebsonsecurity, globalinitiative, uemcon).
Network embeddedness (how deeply connected a person or a group is within their web of relationships) research in illegal online markets demonstrates these frameworks’ empirical relevance to constrained environments (bjc). Duxbury and Haynie’s (2023) analysis of drug purchasing diversity on illegal platforms reveals endogenous pricing and profit mechanisms that correspond to strategic framework predictions, supporting the theoretical transposition (ser).
2.3 Christensen’s Disruptive Innovation Theory
Christensen’s disruptive innovation theory provides essential frameworks for understanding market transformation through initially inferior solutions that excel in overlooked dimensions (hbs, jms). The theory distinguishes between:
- Low-end disruption: targeting overserved segments with simplified, accessible alternatives.
- New-market disruption: enabling previously excluded participants through novel value propositions.
Central to the framework is the performance trajectory model, which demonstrates how sustaining innovations often exceed market requirements, creating opportunities for “good enough” solutions that trade traditional performance metrics for accessibility, convenience, or cost reduction.
The innovator’s dilemma emerges when established players focus on sustaining innovations serving demanding customers while missing disruptive opportunities in underserved segments.
Asymmetric business models enable disruptive competitors to operate under different economic logic than established players, competing through alternative value networks that prioritize different performance criteria.
These models typically begin with simplified offerings serving non-consumers or low-end segments, gradually developing capabilities to move upmarket while established competitors remain focused on high-end customer demands.
The theory’s predictive power lies in recognizing that initial performance inferiority often masks superior strategic positioning, as disruptive innovations improve along different trajectories that eventually intersect with mainstream market requirements.
2.4 Bridging disruptive strategies: the Four Actions Framework mapping
The analysis of disruptive strategies main theories reveals bridges between Blue Ocean Strategy’s four actions and both Christensen’s and Teece’s frameworks.
Christensen’s Disruptive Innovation Equivalents (christensen, hbs2):
- ELIMINATE → Market Overservice Rejection: Disruptive innovations systematically eliminate features that overserve low-end market segments, creating accessibility for non-consumers
- REDUCE → Complexity and Cost Reduction: Initial offerings sacrifice traditional performance metrics while excelling in simplicity and affordability
- RAISE → Accessibility and Convenience Enhancement: Focused improvement on factors critical to underserved segments
- CREATE → New Market Segment Generation: “New-market disruption” through entirely novel consumer categories
Teece’s Business Model Innovation Equivalents (lrp):
- ELIMINATE → Value Leakage Reduction: Removing costly value chain activities that don’t enhance customer value proposition
- REDUCE → Transaction Cost Minimization: Streamlining value delivery through dynamic capabilities deployment
- RAISE → Value Capture Enhancement: Elevating revenue model effectiveness and customer willingness to pay
- CREATE → Novel Value Architecture: Unprecedented value creation mechanisms through business model innovation
Building these bridges allow to identify, analyze, explain and predict more comprehensively cybercriminal disruptive strategies.
3. Transposition Analysis
The transposition of business strategy frameworks to cybercriminal analysis succeeds where criminal organizations operate under market logic rather than hierarchical command structures. The enterprise model of organized crime (or business models of organized crime) treats criminal organizations as businesses operating under unique constraints (unodc).
3.1 Market creation mechanisms
Blue Ocean Strategy’s six paths framework maps remarkably well onto cybercriminal market creation strategies.
Silk Road turned the drug trade from a local, in-person activity into a global, 24/7 online marketplace by breaking down the usual limits of distance and time, generating $1.2 billion in transactions through systematic elimination of traditional drug trade friction points (usice).
REvil’s affiliate structure demonstrates classic platform strategy implementation, creating two-sided markets with network effects, performance metrics, and revenue sharing that parallel legitimate business partnerships. Their documented affiliate earnings growth from $20,000-30,000 to $7-8 million per target within six months represents successful scaling through strategic framework application (intel471, paloalto).
3.2 Six Paths examples across Threat Actor types
The following empirical examples illustrate how cybercriminal organizations, state-sponsored groups, and hacktivist collectives systematically reconstruct industry boundaries to create strategic advantages. Each case reveals an underlying (conscious or unconscious) strategic move that parallels legitimate business innovation while exploiting unique criminal capabilities.
The Blue Ocean’s six paths provide direction on where to look for opportunities, when Blue Ocean’s four actions provide the blueprint on how to execute the business model.
Path 1: Looking Across Alternative Industries | Silk Road
From Traditional Drug Distribution to Silk Road
Ross Ulbricht analyzed alternatives to street-level drug distribution. Traditional alternatives expose buyer to Street dealers, dark alleys, physical risk, quality uncertainty. Looking at the e-commerce industry, he reconstruct its characteristics and created an online marketplace for drug distribution with reputation systems, quality assurance, and geographic safety.
- 4 Actions Implementation:
- ELIMINATE: Physical risk, quality uncertainty, geographic limitations
- REDUCE: Transaction costs, time investment, legal exposure
- RAISE: Product quality standards, customer service, selection variety
- CREATE: Anonymous online marketplace with built-in escrow and reputation systems
While Silk Road demonstrates marketplace innovation, strategic group analysis reveals different patterns in state-sponsored contexts.
Path 2: Looking Across Strategic Groups | APT1
APT1 (Comment Crew) disrupting traditional cyberespionage groups
APT1 sponsor’s probably looked across threat actors in cyber espionage landscape. It was basically composed of:
- High-end group: Sophisticated, surgical, minimal footprint operations (like Equation Group)
- Low-end group: Opportunistic, noisy, volume-based operations
The organizational pattern and modus operandi of APT1 reveals a “industrial espionage at scale” choice: systematic, persistent, but not overly sophisticated.
- 4 Actions Implementation:
- ELIMINATE: Expensive zero-day development, surgical precision requirements
- REDUCE: Operational complexity, attribution avoidance costs
- RAISE: Volume and persistence, systematic target coverage
- CREATE: “Good enough” espionage model with acceptable attribution risk
Beyond strategic positioning, the reconstruction of buyer chains may create a whole new criminal service categories.
Path 3: Looking Across Buyer Chains | IAB
Initial Access Brokers (IABs) insert into direct criminal operations
The earliest known threat actor or group to specialize in breaching systems for later resale is unknown in public academic and industry sources. The role of IABs probably evolved gradually within cybercrime as online criminal forums matured and ransomware-as-a-service models began to grow (keliacyber, reliaquest).
Well-inspired individual or groups specialized in initial access should have notice opportunity in the intrusion-based cybercriminal buyer chain. The traditional chain was integrated group with exploitation of all its internal capacity to perform direct attack against the target: initial access, tool development, vulnerability research, intrusion, money laundering.
Breaking down the chain, we can separate the chain in four main stage : specialists → criminal group → attack execution → exfiltration. IAB birth lays in the specialist group, were specialization creates value for multiple buyer types (ransomware, financial threat, botnet operator, state-sponsored actors, …).
- 4 Actions Implementation:
- ELIMINATE: Need for each group to develop initial access capabilities
- REDUCE: Time-to-attack for ransomware operators, specialization costs
- RAISE: Access quality and reliability, targeting precision
- CREATE: Professional breach-as-a-service marketplace
Aside the buyer chain, complementary service integration represents another dimension of criminal perimeter reconstruction.
Path 4: Looking Across Complementary Offerings | Emotet
How Emotet replace Single-Purpose Malware
Emotet is a response to complementary services in malware-based cybercrime that coexist to enable an operationnal capabitity: downloader/dropper, backdoor, keylogger, grabber, … and the network infrastructure needed to support orchestration of those capacities.
In this context, Emotet created a modular platform serving multiple criminal use cases with an Infrastructure-as-a-Service models.
- 4 Actions Implementation:
- ELIMINATE: Need for separate infrastructure for each criminal service
- REDUCE: Infrastructure development costs for other criminal groups
- RAISE: Reliability, scale, and professional service delivery
- CREATE: Modular criminal platform with plugin architecture
But in business, everything is not based on pure calculus, and emotion do also have its market space. The functional-emotional orientation shift illustrate how criminal organizations can transcend physical operation.
Path 5: Looking Across Functional-Emotional Orientation | Anonymous
Anonymous blending traditional cybercrime operation and political activism
Anonymous crossed functional-emotional boundaries of two unrelated space:
- Traditional functional: Technical hacking for criminal/espionage purposes
- Traditional emotional: Political activism through legal means
By combined technical capabilities with ideological messaging they propulsed hacktivism to a new cyber threat dimension.
- 4 Actions Implementation:
- ELIMINATE: Hierarchical organization, formal membership requirements
- REDUCE: Technical barriers to participation, coordination overhead
- RAISE: Emotional engagement, media impact, symbolic value
- CREATE: Decentralized “hacktivist” model with memetic brand identity
Finally, criminal organizations can not only exploit emotion but also temporal dimension to gain timing advantages unavailable to legitimate competitors.
Path 6: Looking Across Time | APT28
APT28 (Sandworm/GRU) reshape traditional (cyber)warfare
The GRU, Russia’s military intelligence service, are by default tied to temporal boundaries of cyber operations. Traditionally, you would use cyberwarfare during active military conflicts. But you can also use it during peacetime against your frenemy.
This create a “not-quite-war” cyber operations below conflict threshold, that we can be compared to the “Guerasimov framework” and the “gray zone warfare” concepts (milspec, smallwarsjournal, usarmy).
- 4 Actions Implementation:
- ELIMINATE: Direct attribution requirements, formal conflict justification
- REDUCE: International incident escalation risk, diplomatic costs
- RAISE: Economic damage capability, strategic disruption impact
- CREATE: “Hybrid warfare” model combining criminal cover with state objectives
These diverse applications illustrate that Blue Ocean Strategy’s 6 Paths framework transcends traditional industry boundaries to explain strategic behavior across criminal contexts. The consistent pattern of boundary reconstruction (whether in cybercrime, hacktivism, state-sopnsored operation) reveals the strategic capabilities of modern threat actors. This open the door for for future research to confirm that both profit-driven criminals and state-sponsored actors apply similar strategic logic, though with different objectives and constraints.
3.3 Limitations
Framework limitations emerge where criminal organizations possess capabilities unavailable to legitimate enterprises, primarily violence and complete regulatory circumvention. Traditional competitive analysis breaks down when competitors can physically eliminate rivals or operate with complete disregard for legal constraints (usojp, unicri).
Porter’s Five Forces, the most basic, widely-accepted business framework, requires modification to account for violence as a competitive weapon and law enforcement as an external force affecting all market participants (cyr).
The regulatory arbitrage dimension requires theoretical extension beyond standard business strategy frameworks (clsc, candoj). Criminal organizations systematically exploit jurisdictional gaps, legal ambiguities, and enforcement limitations (passas). Those capabilities lack direct analogues in legitimate business strategy. This represents a fundamental limitation requiring criminology-specific theoretical development.
4. Criminal Modeling
The integration of business strategy frameworks with criminal organizational analysis produces the following theoretical model with five core components:
Market creation
Market creation mechanisms operate through systematic boundary reconstruction, parallel to Blue Ocean Strategy’s six paths but adapted for illegal contexts. Criminal organizations create uncontested market spaces by exploiting regulatory gaps, technological innovations, and geographical arbitrage opportunities. The darknet marketplace evolution demonstrates this pattern from Silk Road’s initial market creation through successive platform innovations addressing security, payment, and trust challenges.
Value innovation
The value innovation Processes in criminal contexts involve simultaneous risk reduction and service enhancement. The Conti group’s documented customer service approach (including negotiation protocols, data recovery guarantees, and professional communication standards) exemplifies value innovation in illegal markets. Their approach to victim transforms ransomware from pure extortion into a service relationship, demonstrating sophisticated understanding of customer value propositions (cyr2).
Network effect and ecosystems developments
Network Effects and Ecosystem Development manifest through criminal organizations’ systematic building of supporting infrastructure. The growth of Initial Access Brokers (IABs) represents network effect creation—as more criminal groups demand initial access, specialized brokers develop capabilities that benefit the entire ecosystem. CrowdStrike’s 2023 Threat Report documentation of 147% growth in IAB advertisements demonstrates ecosystem maturation through network effects (sans).
Regulatory arbitrage
Regulatory arbitrage extend beyond traditional business concepts to include systematic exploitation of legal system limitations. Criminal organizations operate across multiple jurisdictions simultaneously, timing operations to exploit regulatory lag periods, and leveraging technology gaps to create operational advantages. This represents a theoretical extension of legitimate regulatory arbitrage into domains unavailable to lawful enterprises.
Adaptation
Adaptation mechanisms demonstrate abilities to learn, change and develop new skills (dynamic capabilities) facing extreme pressure, with criminal organizations showing remarkable resilience when facing law enforcement disruption. The Conti group’s organizational survival after multiple law enforcement actions, including the documented succession planning that led to Black Basta and Karakurt formation, illustrates sophisticated organizational learning and adaptation capabilities.
5. The Conti Case Analysis
The Conti ransomware group represents the most empirically documented case of sophisticated cybercriminal strategic behavior, with 60,000+ leaked internal communications providing unprecedented visibility into criminal organizational strategy. Operating from 2020-2022, Conti generated $180 million through systematic application of business strategy principles (coveware, krebsonsecurity, uemcon)
5.1 Conti strategy analysis
Organizational structure and management
Conti operated with clear hierarchical management including CEO-equivalent leadership (“Stern/Demon”), department managers (“Mango” as senior manager), and specialized divisions for HR, R&D, and operations. The organization employed 500+ members at peak operations with fixed salary structures ($1,000-2,000 monthly) rather than percentage-based affiliate models, demonstrating purposeful human resource management.
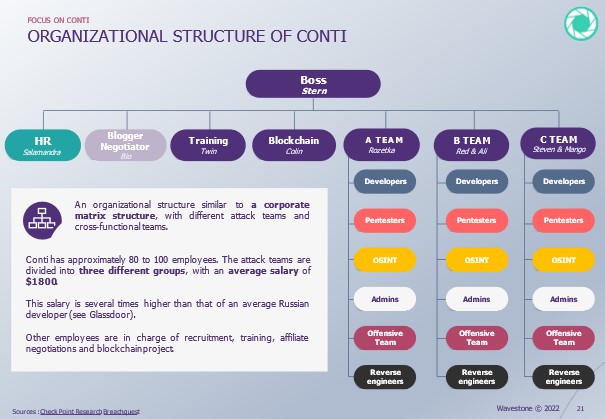 Organizational chart of the Conti group (wavestone)
Organizational chart of the Conti group (wavestone)
Innovation and market creation
Conti pioneered the double extortion model, combining traditional encryption with data theft to create multiple revenue streams. This innovation represents classic Blue Ocean Strategy application: creating uncontested market space by combining previously separate criminal services. The group’s simultaneous operation of Emotet botnet infrastructure shows vertical integration strategies typical of legitimate enterprises.
Competitive positioning and market leadership
During 2020-2021, Conti dominated the ransomware market, generating double the revenue of nearest competitor DarkSide (globalinitiative). The organization’s professional “customer service” approach to victim negotiations, including standardized communication protocols and data recovery guarantees, created competitive differentiation through service quality, a by-the-book application of value innovation principles.
Dynamic capabilities and adaptation
Conti demonstrated remarkable organizational learning and adaptation capabilities. When facing increased law enforcement pressure, the group modified operational procedures, enhanced security protocols, and ultimately executed succession planning that fragmented the organization into multiple successor groups (Black Basta, Royal, Karakurt) to preserve organizational knowledge and capabilities.
5.2 Disruptive strategy analysis
Conti followed classic NEW-MARKET disruption patterns. They created a new consumer category, moving from purely criminal victims to “business service customers” requiring professional data recovery and reputation management. Early ransomware was becoming too complex and unreliable for victims to pay, asking them to use prepaid card system, access the ransom gang via the Tor network or perform Bitcoin transfer. Conti’s professional approach made ransomware “payments” more reliable and predictable. This disruption allows to move the market up, and go from opportunistic individual ransoming to corporate “Big Game Hunting” targeting.
According to Teece’s Dynamic Capabilities in Conti’s case, we can breakdown their strategy as follow.
SENSING – Identify the 6 Paths Opportunity
Conti’s leadership systematically monitored victim response patterns, law enforcement priorities, and competitor strategies through their intelligence gathering network. A smart analysis of pre-conti leaked victim communications showed traditional ransomware created single-point negotiation pressure, while data breaches affected multiple stakeholders. This sensing enabled the buyer chain reconstruction insight (Path 3).
SEIZING – Implementing 4 Actions Framework
Conti rapidly mobilized organizational resources to implement double extortion. They managed to develop a dual infrastructure (encryption + exfiltration tools) and new operational procedures (leak site management, multi-stakeholder pressure). The key HR structure enabled quick skill acquisition and process standardization.
TRANSFORMING – Continuous Adaptation
Conti continuously refined their approach based on victim responses and competitive pressure. They gradually evolved from manual to automated negotiation systems, and development of victim-specific pressure strategies. This enabled sustained competitive advantage through continuous innovation, beating the innovator’s dilemma.
Yet, they ultimately fell victim to factors outside traditional business strategy: geopolitical tensions, internal betrayal, and law enforcement pressure (hackernews, bushidotoken).
6. Edge Cases
Conti’s planned “phoenix” rebranding into smaller groups groups demonstrates that while disruptive strategic frameworks can explain criminal innovation and market disruption, they cannot account for the fundamental instabilities inherent in operating outside legal boundaries, making such theoretical applications analytically valuable but ultimately incomplete.
An industry of violence
Business strategy framework transposition also fails under specific conditions that highlight theoretical boundaries. Violence capabilities represent the most significant limitation: when criminal organizations resort to physical threats or elimination of competitors, traditional competitive analysis breaks down completely. The framework assumes rational economic actors operating under legal constraints, conditions absent in criminal contexts.
State-criminal hybrids
State-sponsored actor integration presents complex edge cases. The Lazarus Group’s evolution from pure espionage to revenue generation ($6 billion stolen since 2017) illustrates that hybrid models complicate classical framework application, from a business and a criminological perspective (microsoft). When criminal organizations operate with state backing, traditional resource constraints and competitive dynamics no longer apply, requiring separate theoretical treatment.
Regulatory arbitrage as fuel
Complete regulatory circumvention represents a theoretical limitations where criminal organizations operate beyond any legal framework constraints. Unlike legitimate businesses that engage in regulatory arbitrage within legal boundaries, criminal organizations can completely ignore regulatory restrictions, and even innovate or create new products and markets by circumventing them. This capability fundamentally alters competitive dynamics and strategic possibilities in ways not addressed by traditional business strategy theory.
Weakened network effect
Criminal network effects can collapse rapidly under law enforcement pressure in ways that legitimate network effects do not. The Silk Road takedown demonstrated how criminal network effects lack the resilience of legitimate platforms: when law enforcement simply captures core infrastructure, entire ecosystems can disappear instantly. Legitimate businesses face bankruptcy proceedings and asset transfers; criminal networks face complete operational termination.
Organizational Learning Limitations
While criminal organizations demonstrate sophisticated organizational learning, knowledge transfer faces unique constraints. Security requirements limit information sharing, high member turnover reduces institutional memory, and law enforcement targeting disrupts knowledge preservation mechanisms (csr).These limitations do not affect legitimate organizations to the same degree.
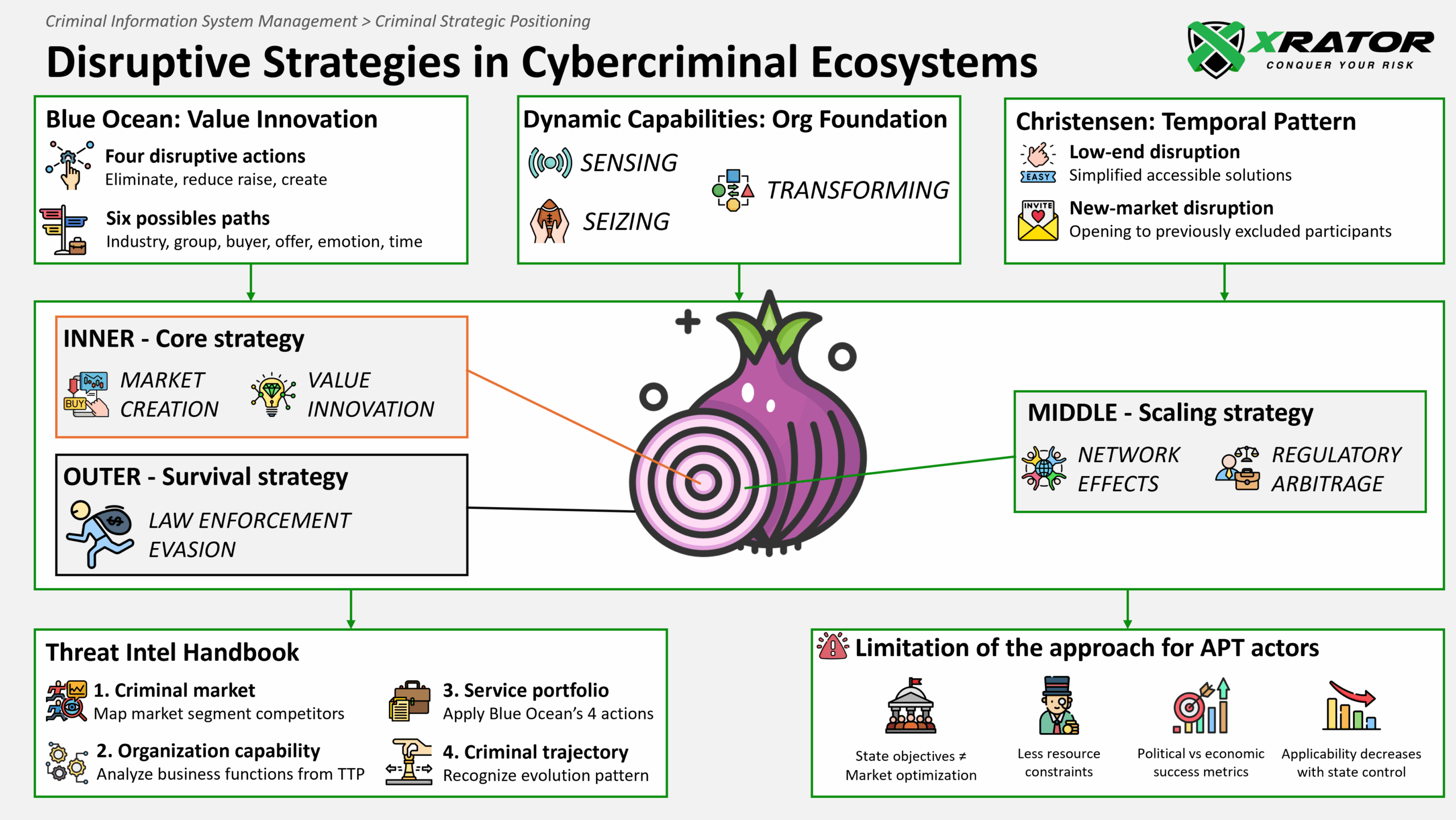
7. Threat Intel application: competitive dynamics assessment
CTI practitioners already know how to analyze what threat actors do technically (their TTPs, tools, infrastructure). This methodology analyzes why attacker group do it and how they organize to do it, determining their business strategy. We can refer to this assessment as adding a “business intelligence” layer to existing technical intelligence practices.
7.1 Phase 1: Market Landscape Mapping
Phase 1 market mapping reveals Blue Ocean Strategy’s 6 Paths framework in action. RansomHub’s market leadership emergence demonstrates classic strategic group analysis. They positioned themselves between the high-sophistication LockBit model and simpler ransomware operations, creating competitive differentiation through “good enough” service quality. This mirrors Christensen’s disruptive innovation patterns where new market leaders succeed through strategic positioning rather than superior technology.
First, we need to identify which criminal market your target operates in. We can start for example with this two segment, then incremente the market segment list:
- Ransomware Market: Groups that encrypt and/or steal corporate data for ransom
- Business Email Compromise (BEC) Market: Groups targeting financial fraud through email manipulation
Starting from the selected list of cybercriminal market segment, we map involved groups using public sources: ransomware leak aggregator, security vendor reports, or underground forum monitoring services. With a list of 3-5 competitor per segment, we further create a simple table: Group Name, Active Status, Estimated Victim Count, Primary Target Types, Last Major Campaign.
RansomHub example: Vendor report of Q1 2025 shows RansomHub as market leader with X% of incidents. Compare against competitors like Play, LockBit remnants, and newer entrants. Note their rise correlates with LockBit’s law enforcement disruption.
7.2 Phase 2: Business Function Analysis
Phase 2 organizational analysis exposes Teece’s dynamic capabilities. RansomHub’s rapid scaling post-LockBit disruption demonstrates sophisticated sensing capabilities (identifying market opportunity), seizing capabilities (mobilizing resources to capture market share), and transforming capabilities (adapting operations for sustained leadership). The business function mapping will reveals organizational sophistication that can contradicts, or not, initial assumptions about criminal group capabilities.
Here we will need to translate technical observations into business roles for each competitors. As it is not a natural exercises for CTI specialists, we can start by using this conversion guide:
- Custom malware variants → R&D capability
- Victim communications → Customer service function
- Standardized ransom notes/payment sites → Marketing/branding function
- Multiple simultaneous campaigns → Operations scaling capability
- Recruitment posts → HR/talent acquisition function
- Affiliate payment systems → Finance/accounting function
RansomHub example: Their professional ransom note templates and victim negotiation portals indicate dedicated customer service. Multiple simultaneous high-profile attacks suggest operational scaling. Affiliate recruitment indicates HR function. Evidence of code reuse across campaigns suggests R&D standardization.
Once we mapped our technical and tactical knowledge about a threat actor into business function, we are ready to profile the organizational structure. We will look for hierarchy indicators in communications (formal vs informal language), role specialization (different people handling different campaign phases), and decision-making patterns (single spokesperson vs multiple). We use a three categorization : Flat Network | Hierarchical | Hybrid Platform.
7.3 Phase 3: Service Portfolio Analysis (45 minutes)
Phase 3 service portfolio analysis directly applies Blue Ocean’s four actions framework. RansomHub eliminated complex victim negotiation processes, reduced technical barriers for affiliates, raised service reliability standards above fragmented post-LockBit competition, and created streamlined attack-to-payment workflows. This value innovation enabled rapid market share capture through strategic differentiation rather than pure technical superiority.
During this step we will need to identify core business services for each competitors. Again, as it is not a natural exercises for CTI specialists, we can start by using this standard criminal service taxonomy and refine later:
- Access Services: Initial network compromise, credential theft
- Persistence Services: Maintaining long-term access, establishing footholds
- Extraction Services: Data theft, intellectual property acquisition
- Disruption Services: System encryption, operational interruption
- Negotiation Services: Victim communication, payment processing
- Support Services: Technical assistance, decryption guarantees
For each service category, we document what the group offers based on observed TTPs or communication:
- Access: Custom phishing, vulnerability exploitation, credential stuffing
- Persistence: Living-off-the-land techniques, custom implants
- Extraction: Automated data collection, selective targeting
- Disruption: Encryption capabilities, system destruction
- Negotiation: Professional communications, flexible payment terms
- Support: Decryption testing, technical support chat
RansomHub example: Strong access services (multiple initial vectors), sophisticated extraction (selective data theft), professional negotiation services (standardized communication), reliable support services (decryption guarantees). Weak persistence services (focus on quick encryption rather than long-term access).
Finally we can compare service portfolio between competitors of the same segment (or cross segment to go even further) with a key quesion in mind : What do they do differently? For example, we assess that RansomHub differentiates through faster victim processing and higher reliability compared to post-LockBit ransomware market offerings.
7.4 Phase 4: Strategic Pattern Recognition
Pattern with not necessarily appear at the first assess, but on the medium to long run. We need to track these specific adaptation indicators over time:
- Victim targeting evolution: Changes in industry focus, company size, geographic regions
- Technical capability progression: New attack vectors, improved evasion, enhanced automation
- Service delivery improvements: Faster encryption, better victim communication, payment processing
- Competitive responses: Copying competitor innovations, defensive reactions to market changes
- Operational security adaptations: Response to law enforcement actions, defensive countermeasures
RansomHub example: Monitor their response to increased law enforcement focus post-LockBit takedown. Track whether they maintain current service levels or adapt to reduce visibility. Watch for competitive responses as other groups attempt to capture market share.
Based on observed patterns, we can predict likely evolution and perform a trajectory assessment:
- Service expansion (new capabilities)
- Market consolidation (acquiring smaller competitors)
- Operational adaptation (improved security measures)
- Geographic expansion (new target regions)
In conclusion, Phase 4 adaptation tracking reveals the criminal modeling dimensions we identified. RansomHub demonstrates regulatory arbitrage (exploiting law enforcement actions against LockBit to emerge as a leader), network effects exploitation (building affiliate ecosystems), and strategic adaptation mechanisms (evolving operational security in response to increased scrutiny). Their trajectory suggests a criminal organization with a supra-adaptative strategy maturity, able or close creating entirely new criminal market categories, combine criminal with legitimate business practices, and/or transferring capabilities across organizational incarnations.
7.5 Predictive intelligence implications
Organizations demonstrating systematic Blue Ocean strategy application (like RansomHub’s market positioning) typically follow predictable evolution paths: initial market capture through service differentiation, gradual capability enhancement through organizational learning, and eventual ecosystem development through platform strategies. This suggests RansomHub will likely develop more sophisticated affiliate management, expand service offerings, and potentially face disruption from new entrants applying similar strategic frameworks.
This proposed methodology contributes in transforming tactical threat intelligence into strategic prediction. Instead of asking “what will RansomHub attack next,” analysts can ask “how will RansomHub evolve their business model” and “what strategic vulnerabilities enable effective disruption.” This shift from tactical to strategic thinking enables proactive defense planning based on organizational logic rather than technical indicators alone.
8. Conclusion
Disruptive strategies frameworks emphasize strategic and processual analysis while underemphasizing technological constraints and human behavioral factors specific to criminal operational security requirements.
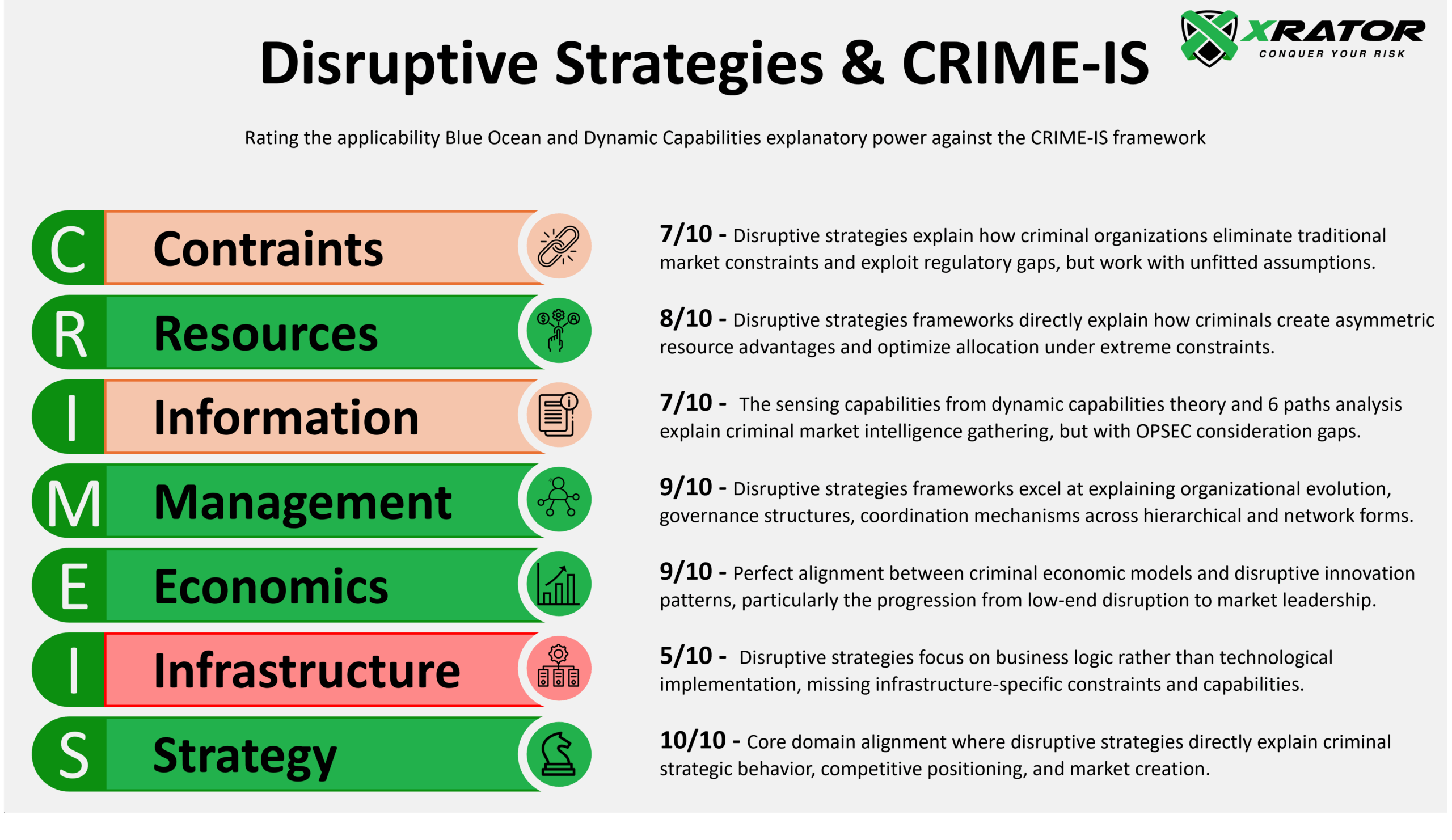
The profit versus political motivation divide creates the fundamental applicability boundary for disruptive strategies frameworks. Cybercriminal organizations operate under market logic with resource constraints, competitive pressures, and economic optimization—conditions where disruptive innovation naturally occurs. APT groups function as state extensions with different success metrics, unlimited resources, and political rather than economic objectives that fundamentally alter strategic logic.
| Threat Taxonomy | Cybercrime | APT | Explanation |
| Level 1 Individual actors | 2/10 | 0/10 | Insufficient organizational complexity for strategic frameworks across both contexts. |
| Level 2 Small groups | 4/10 | 2/10 | Limited strategic capabilities with minimal APT and basic cybercrime thinking. |
| Level 3 Formal org. | 8/10 | 5/10 | Moderate applicability with cybercrime exceeding APT due to constraints. |
| Level 4 Ecosystems | 9/10 | 3/10 | Strong cybercrime market dynamics versus weak APT state coordination. |
| Level 5 Service platforms | 10/10 | 1/10 | Maximum divergence: perfect cybercrime fit versus minimal APT relevance. |
The five-level taxonomy proves highly relevant for distinguishing strategic sophistication, but cybercrime organizations consistently demonstrate higher disruptive strategy applicability at equivalent organizational levels. This suggests that market-driven constraints, not organizational complexity alone, determine whether sophisticated organizational capabilities translate into business-strategic behavior. The taxonomy effectively captures organizational evolution patterns while the profit/political distinction determines strategic framework relevance. Unlike APT groups following state directives, profit-driven criminal organizations systematically apply disruptive innovation patterns that enable prediction of their strategic evolution, but not their tactical implementations.
Understanding that groups like RansomHub follow blue ocean strategy principles means analysts can anticipate market positioning changes, service innovation directions, and competitive responses to defensive measures. This predictability enables proactive defense planning focused on disrupting criminal business models rather than just blocking current attack vectors.
The framework’s limitation to profit-driven adversaries actually enhances its utility by clearly defining when it provides predictive value versus when traditional geopolitical analysis remains necessary for state-sponsored threats.


