Abstract
- The first ransomware has been created in 1989 and was full of flaws;
- The cybercrime industry gradually improves the product to create a multi-billion dollars blackmail segment;
- The obvious disruptive nature of ransomware makes the world realized the strategical role played by information technologies;
- The Digital Transformation reposition IT from an operational to a transversal strategical risk;
- Cybersecurity, with ecology and demography, are the three challenges of this century.
Introduction
Ransomware attacks are making the headlines for some years now, and the covid-19 crisis demonstrates the systemic risks that it brings to corporation and societies. Infection and disruption of Critical Infrastructure networks and Hospitals Information Systems made obvious the fact that IT operation are strategic to organization and are contributing to their value creation.
We have seen during the few past years corporate and governments networks adapting their cyberdefense strategy to counter this type of operations, and we can only hope that it will encompass the full cyberattacks spectrum. Ransomwares are indeed only a partial part of the danger any interconnected network can face.
As cybersecurity and cyber risk professional, we need to understand this phenomenon at a macro scale and what aspects of it strikes decision-maker to the point of unlocking a general awareness, countermeasures, and budget allocation. To answer this question, we need to look at these events from several perspective and assess how the potential visible and immediate impacts on economics and societies are playing a role in this global fight against cybercrime.
The evolution of Ransomware Operation and Business Model
Ransomware didn’t stop to evolve since the end of the 1980’s and turned from a tiny criminal operation to a multi-billion dollars blackmail industry. Looking at the evolution of Information Technology adoption and Ransomware in parallel allow to understand the fundamentals of this criminal segment and may help us to understand its future path as well as other malicious use of technology.
1. A slow and weak criminal Proof of concept
We can find the origin of ransomware back to 1989 with the AIDS ransomware, with the basic modus operandi that is still the basic skeleton of any disruption-based blackmail operation. A malicious software block access to the data and ask for a fee to unlock it. In the AIDS Ransomware case, its creator Joseph Popp use symmetric encryption to scramble access to data.
The first limitation of this operation was the use of symmetric encryption. Indeed, as it was the very same key that was used to encrypt then decrypt the data. And for the encryption to happened, that key needed necessary to be on the computer. A trained system administrator would have little difficulties to search for it in the infected hosts then use it to decrypt the data without having to pay the ransom.
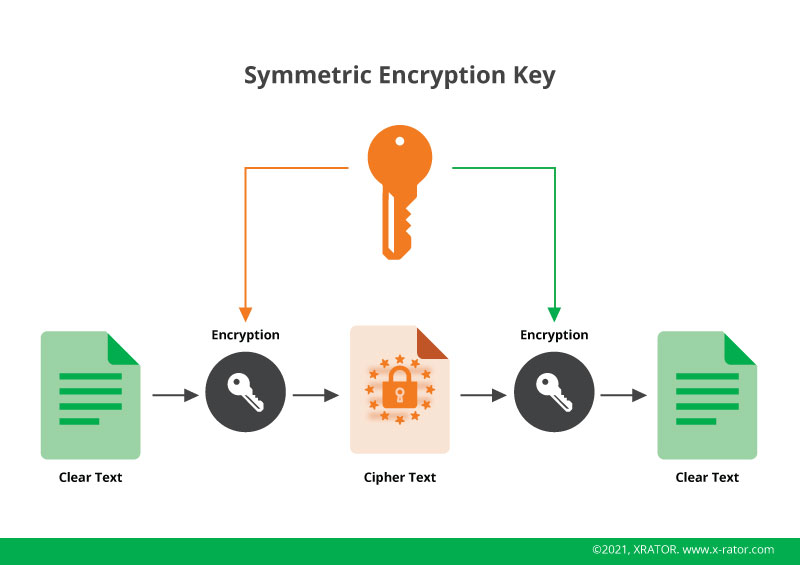
The second limitation was the targeted market. Internet accesses and computer were still a luxury at that time and with a very limited bandwidth. The techniques were then to use infected floppy disk. So you needed to hack into a niche of users with physical medium. Needless to say the return of investment was to low and the risk taking was to high to be sustainable.
The third limitation was the traceability of the money flows. The ransom had to send to a postal mailbox and would be deposit to a bank account, which made it pretty easy for Law Enforcement or Banking Institution to investigate and mitigate the behavior.
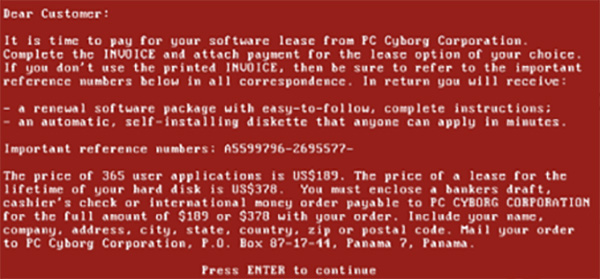
This ransomware genesis allows us yet to identify crucial factors for a successful and longstanding ransomware operation:
- A sufficient amount of potential victims;
- A digital way of distribution for a broaden access and infection speed;
- A more robust encryption method;
- A less traceable mean of payment.
This is basically e-commerce 101 blueprint.
2. IEEE and the birth of the modern cryptovirus concept
In 1996, two researchers published a paper at the IEEE Symposium on Security and Privacy where they invented the concept of cryptovirology: the use by rogue software of cryptography to boost its offensive capabilities. Apart from creating a new path in computer security research, the innovation they brought was the use of asymmetric cryptography by a ransomware (that they coined “cryptovirological attacks”), meaning that the key to encrypt the data on the computer (the “public-key”) was not the same as the key used to decrypt the data (the “private-key”).
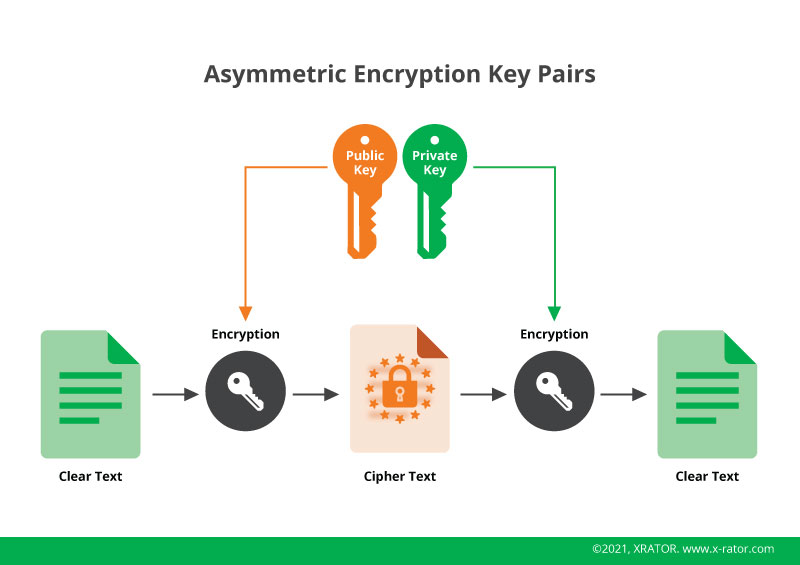
The first innovation fixed a pain point of former ransomware encryption methods, as now only the public-key would be brought by the rogue software into the computer and was of no help to solve the problem of our benevolent system administrator. The private key, the only one that could free the data, stayed outside of the victim’s environment.
The second innovation dealt with the propagation method. Former ransomware should be inserted one by one with a physical medium. Their cryptovirological attacks leverage the infection methods of computer virus. A computer virus is a malicious program that insert itself into a legitimate file. So that when you copy or transfer that file, the virus follows.
This evolution still holds four main drawback for a lucrative cybercriminal operation:
- The still low amount of potential victims;
- The traceable payment method;
- The transaction reversing potential.
And a forth one introduced by the researcher themselves: this solution stayed in academic circle and did not reach the general cybercriminal public until 2013 and the rise of the infamous Cryptolocker.
Until there, ransomware used another disruption techniques, called “Locker”. A kind of malicious software that is still asking for money but replace data encryption with screen locking as a pressure point. They generally posed as Police Warning for illegal internet activities, asking to pay, you guess it, a fee. “Locker” are also coined as scareware (scaring software) as they leverage the fear of the user to produce a reaction.
Scarewares were everywhere at the end of the 2000’s, from rogue antivirus to fake windows speed optimizer. Later ransomware gangs come from this trends, meaning they are operationally experienced and well-funded.
3. Ransomware-as-a-Service and the rise of Big Game Hunting
If ransomware at the end of the 2000’s decade and the very beginning of the 2010’s shifted the payment method to use various alternative less traceable that hardcoded bank account (such as gift card or electronic cash system like Liberty Reserve) the invention of Blockchain and its associated transaction system Bitcoin in 2008 vastly solve the unreversible money flow required by that kind of criminal activity.
Ransomware also vastly benefits from the spam and botnet industry maturation of the 2000’s decade, bringing new opportunity to spread malicious payload to the now vast population of internet users. Either the cybercriminal buy the access to an infected computer to push its rogue software, either he rent the power of a spamming infrastructure to reach by email its potential victims and perform social engineering to convince them to open a trapped attachment or a malicious web link.
But ransomware also suffers from the development of spam and botnet : Law Enforcement Takedown. Cyber Police around the world are keener and more capable to disrupt cybercriminal operation, dismantle network infrastructure, trace back from source code to individuals. The pain point of cybercriminal are now :
- Maintaining an infrastructure that is hard to shutdown;
- Obfuscate the full traceable nature of the bitcoin payment network;
- Minimize the clues in the operation that can lead to an individual and its arrestation.
The first pain point has been answered by relying more and more on the anonymized peer-to-peer Tor network (a.k.a. “Darknet”). Cryptolocker was one of the first to successfully used it, quickly followed by CTB-Locker, CryptoWall or TeslaCrypt.
To break the traceability of the bitcoin’s blockchain, cybercriminal used another type or services called “Tumbler” or “Mixer”. Those are services that collects bitcoin payment from different sources, then spit them back to destination wallets. Tumblers remunerates themselves by taking a fee on each transaction. Because those Mixer are not perfect and they add additional cost to cybercriminal, some integrated privacy-by-design cryptocurrencies as mean of payment, the most popular alternative being Monero (“XMR”).
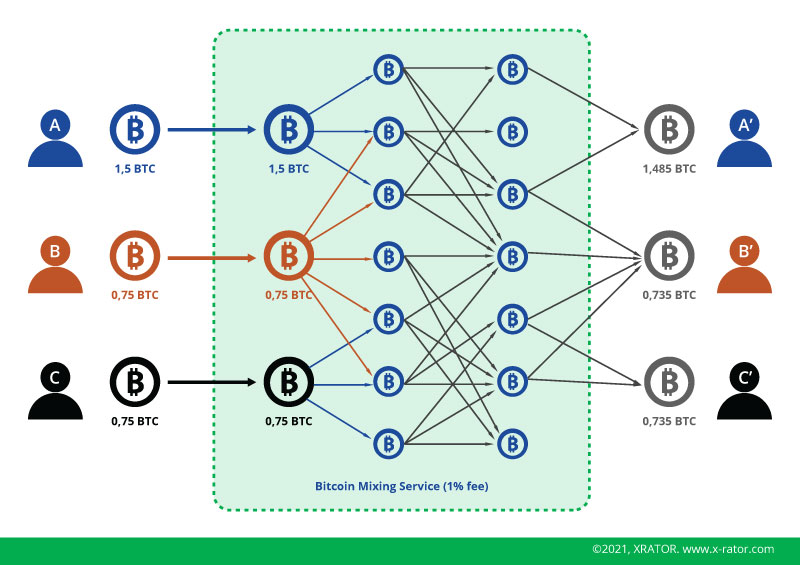
Finally, minimizing clues in code and infrastructure that may lead Law Enforcement to arrest a cybercriminal groups means to have very skilled people on each position that know and understand precisely what they are doing. When in the early days someone could be the software developer, the network administrator, and the spammer, now these are three different people. This trend is common across all cyber threat: specialization and segmentation. In addition, some cybercriminal groups passed deal with the authority of the country were they are based : “we target only victims in opponent countries and you don’t arrest or extradite us”.
The common organization architecture of a ransomware operation today is a group of developer that code the ransomware and sell a software license for its customer. The “Affiliates” are purchasing this license and are often sub-renting it to several carefully selected specialized groups. The “Operator” or “Subcontractor” are teams of skilled intruders that can break into networks and then activate from the inside the cryptovirus. The two or three parties are then splitting the ransom according to a contractual basis and a carefully crafted Return over investment equation.
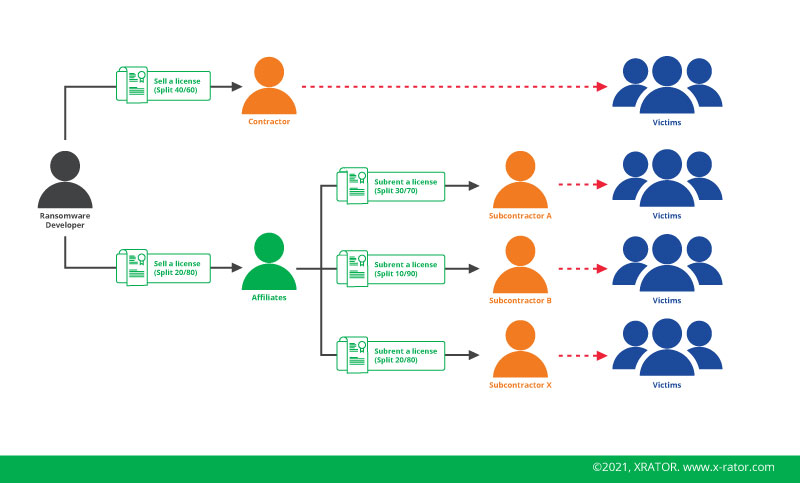
It is also remarkably interesting to notice that the potential victim pool shifts during this period. Before it was private individuals that were blackmail for a few hundred dollars. A mass market predation. Now they moved to target companies that can pay up to several millions of dollars in ransom. A targeted approach.
Corporation may have critical information (Intellectual Property, Confidential Financial Statements, Covered Scandals, …) that can be gathered before activating the ransomware and sold to the highest bidder. The “Ransom-only” business model expand to several source of revenue: selling the hacked entry point to the black-market, trading insider information to the highest bidder, and on top of that a ransom for hundred thousand to millions of dollars. This is the new paradigm that is called “Big Game Hunting”.
Impacts of ransomware operation to the licit society
The evolution of ransomware operation demonstrates a key point that generally split society in two categories: those who understand that cybercrime is first a financial machine that need to structure, adapt, and evolve just like any legal for-profit organization; those who think that cybercrime is perform by hobbyists thrilled by challenge and ego.
1. An awaken from the “Digital Robinhood Myths
From a Risk Management perspective, the perception of the motivation of the threat change everything as we do not respond the same manner to an organized threat or a playful one.
On the one hand, for decades the news media and the entertainment industry show cybercrime with a romantic shade, making the general population unthoughtful about the real danger and impacts of this type of crime on everyday life. The virtual essence of cybercrime makes it more abstract to grasp: “It is not like they were killing anyone!”
On the other hand, information security and cyberdefense professional warned for serious and even sometimes catastrophic scenarios that either do not realized or were lessen by this digital fog. This situation creates a “Cry Wolf” syndrome that may have participate to the denegation of the strategical nature of IT risks.
It seems that the operational disruption that organization suffered during the covid-19 crisis shed a light on how much today’s activities and industries are relying on information technologies. Moreover, its shows that Cyber Risks are not only an operational risk, but also may lead to heavy reputation, regulation, health and safety or financial impacts.
The Digital Transformation of Healthcare and Critical Infrastructure, and the upcoming IT/OT convergence, make people more prone to understand, picture and anticipate critical events involving cybernetics systems. Cyber is a tool, one link in the Global Value Chain, but it is everywhere. It is a strategical one, just as two other main global threats of this century: ecology and demographics. Consciousness is rising to not make it the weakest one.
2. From Cybersecurity to Financial Security and Economic Growth
Ransomware have now a fine-tuned business model and business strategy. The victims they are targeting have been previously reviewed and selected as financially capable organization and they craft the ransom amount according to the due diligence they did before the intrusion and during the intrusion by looking at the accounting and financial internal statements of the company. These financial assets given to cybercriminal are a hole in the investment and expansion strategy of an organization that will have to review its budget allocation.
We must not be defeatist in front of cybercrime, or simply crime. If the society do not evolve, crime do not evolve. And the licit world also reacts to disruption of the criminal assaults. The cybersecurity sector is booming to respond to the level of the threats. What was twenty years ago a technical-oriented economic sector transformed to a multifaceted portfolio of products and services.
Antivirus do now integrate password manager, sandboxed internet browser, website reputation rating. Digital Forensic and Incident Response boost their capabilities with Intelligence and Prospective Approach. The banking and insurance sector are adding new features or offers to their services.
For individual and organization, as a customer, cybersecurity and data privacy are becoming criterion when turning to one solution or another. Brand like Apple made it a winning competitive advantage for at least a decade, making the digital economy following the path of the food, aerospace, or the car industry.
3. A battle for the trust of citizen and customer
One interesting factors of the “Big Game Hunting” business model is that cybercriminal do not treat the victim only as a prey, but also as a customer. Most of their revenue come from the ransom payment, so the trapped individual or organization must be sure that paying will give them back the use of their infrastructure.
This is generally something badly advertise by cybersecurity professional or authorities, that discourage to pay the ransom by stating that you may not receive the decryption keys. But that kind of strategy for a ransomware gang is not long-standing because as soon as the word spread that they are not trustworthy, nobody will pay again. Hence it is not the best argumentation to refrain people from paying.
It is in the very interest of the ransomware gang to be the best “partner in crisis” possible. And it is how we can characterize and rank these groups:
- Are they giving the decryption key?
- In what extend are they ready to offer discount or free of charge payment split?
- Does their recovery method is scalable to a large, encrypted network?
- Do they target you again after the ransom payment?
- Do you find after the payment that some of your information have been dispatch?
Not only does a long-standing gang competes with other to have the best reputation, but they also compete with the advice of security professional and authorities. Just like Serious and Organized crime syndicates do in their environment: they offer something that is more trusted than the response of corporation and government.
The Cybersecurity industry do suffer from time to time since ever from the public distrust. “They are the one that are creating computer virus”, “They sell products and services that did not prevent the intrusion”, “They are taking a commission or billing the negotiation with a ransomware gang”. One point for the cybercriminal.
Authorities and government also struggle with a spreading contestation about their legitimacy, their ability to answer citizen needs, to tackle the socioeconomics, geopolitical and ecological challenges we are all facing. This situation is overly concerning from a criminology point of view, as the history showed it is the root of decades-long powerful crime syndicates.
Conclusion
Ransomwares have for decades an indisputable financial impact. Their associated criminal operation demonstrates the capacity to evolve following technological innovation and economics maturation. This is one sad but fascinating aspect of Criminal Studies, the fact that solution for the common good are often instrumentalize and exploited at illicit ends first.
Criminal organization are just like regular for-profit organization. Starting from a shadowy crew, evolving into a subsidiarized gang and scaling-up to an international consortium. They need a business strategy, to pivot to the more profitable crime while dodging Law Enforcement tracking, dealing with suppliers, and managing contractors. A market. A trustful population. And just like regular for-profit organization, a only few will get to the top.
Today’s most powerful crime syndicates passed their structuration process during the 20 century World Wars period and reach maturity with the financial boom of the 1980’s. Governments were struggling to fulfill the transition needs of part of their population while Authorities were tasked to fight against totalitarianism or ideological concern. Criminals filled the gaps and leverage globalization.
We are in the verge of the cybernetics boom, with a cybercrime industry operating for decades long. Governments are struggling to compose with citizen concerns while Authorities are tasked to fight against terrorism. To prevent the creation of the first real cybermafia, we collectively need to include cybersecurity and cyber risk management in our priorities, to not let cybercriminal win the status of the best (or least bad) “crisis partner”.
Reference
- ZIMBA, Aaron et CHISHIMBA, Mumbi. Understanding the evolution of ransomware: paradigm shifts in attack structures. International Journal of computer network and information security, 2019, vol. 11, no 1, p. 26.
- YOUNG, Adam et YUNG, Moti. Cryptovirology: Extortion-based security threats and countermeasures. In : Proceedings 1996 IEEE Symposium on Security and Privacy. IEEE, 1996. p. 129-140.
- PAKKI, Jaswant. Everything You Ever Wanted to Know About Bitcoin Mixers (But Were Afraid to Ask). 2020. Doctoral dissertation. Arizona State University.
- HERNANDEZ-CASTRO, J., CARTWRIGHT, A., et CARTWRIGHT, E. An economic analysis of ransomware and its welfare consequences. Royal Society open science, 2020, vol. 7, no 3, p. 190023.
- World Economic Forum & PwC, Principles for Board Governance of Cyber Risk. March 2021.
- European Parliament Research Service, Global Trends to 2035 – Geo-politics and international power. September 2017
- Gartner, Gartner Forecasts Worldwide Security and Risk Management Spending to Exceed $150 Billion in 2021. May 2021.
- John Leyden (PortSwigger), Ransomware: Nearly a fifth of victims who pay off extortionists fail to get their data back. March 2021.
- United Nations Office on Drugs and Crime, Causes and Facilitating Factors of Organized Crime. Last consultation: 2021-07-31.


