An investigation has discovered that malicious ads on piracy sites are costing consumers $121 million by tricking people into installing infected devices.
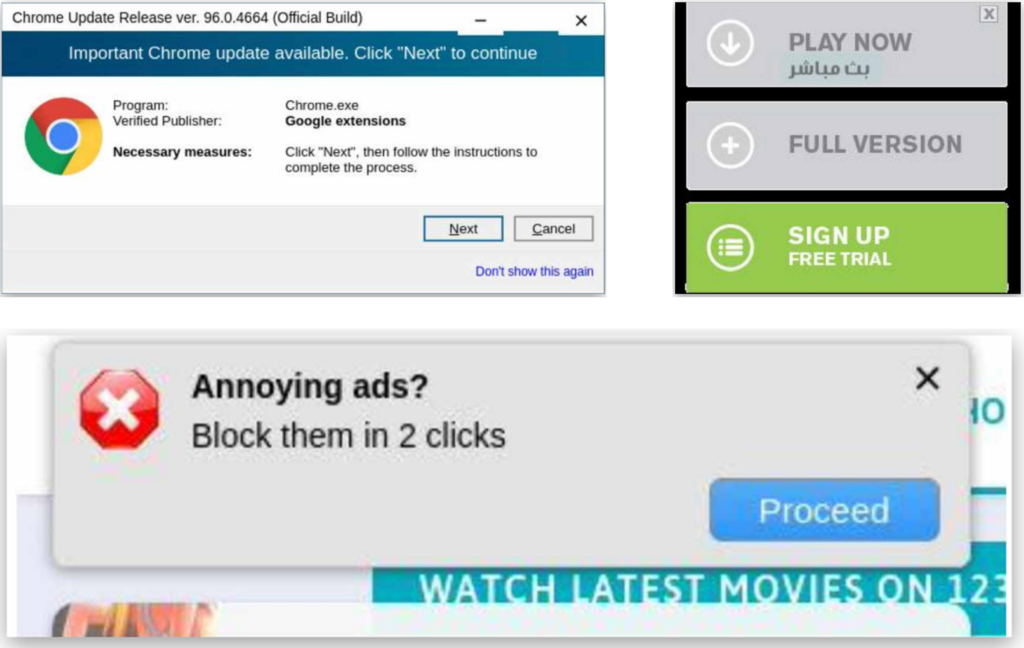
Investigators were hit with ransom ware and other assaults as they investigated; ad intermediaries used scare tactics to entice users into clicking on ads.
Internet users are lured by free content
A new report by the Digital Citizens Alliance, White Bullet, and Unit 221B reveals that visitors to piracy sites are inundated with malicious advertisements that entice them to download malware, including ransomware that takes over files to force victims to pay to regain access. According to the report, ad intermediary companies often promote scare tactics and other dubious methods to trick or entice users to click on dangerous ads, which are frequently enabled by them.
The Unholy Triangle report demonstrates how piracy operators, ad intermediaries, and malvertisers benefit from Internet users lured to suspect sites by the promise of free content. Investigators were lured to a piracy site and were faced with an malicious ransomware attack. When they clicked on an ad, they were confronted with a message that their files had been encrypted, followed by a demand to pay in order to regain access: “All your files like pictures, databases, documents, and other important [sic]data have been encrypted with [sic]the strongest encryption and unique key….Please note that you will never be able to restore your data without paying.”
Investigating the 2 billion dollars piracy business
Tom Galvin, executive director of the Digital Citizens Alliance, believes that ransomware is the most serious cyber threat faced by consumers, small businesses, governments, and corporations. A ‘wake-up call’ has been sounded by the news that piracy operators, malvertisers, and ad intermediaries are profiting by harming Internet users, he says. We must therefore take concerted and coordinated action to combat this growing threat.
The Digital Citizens Alliance has previously estimated that piracy is a $2 billion-plus ecosystem fueled by illicit access to movies, TV shows, and live entertainment. While previous investigations have shown how piracy is used to infect devices, the Unholy Alliance report is the first to detail the relationship between piracy operators, malvertisers, and certain ad intermediaries.
A group of digital citizens, piracy advertising specialist White Bullet, and cybersecurity firm Unit 221B undertook an extensive investigation of thousands of piracy websites, including Fmovies[.]to, Myflixer[.]to, and Dramacool9[.]co. The groups meticulously evaluated advertising and threats on the most-visited piracy websites or those with the most malvertising.
From Advertissement to malware download
Investigatiors asked ad intermediary RichAds if it would accept a ad that was obviously deceptive and would trick users into downloading malware. Even though the ad said that users’ devices had viruses to trick users into downloading “a security tool” that is malware, RichAds approved it.
Piracy services are harming consumers by infecting them with malware, according to Peter Szyszko, CEO and founder of White Bullet. Because we track the value of advertising data on piracy services, we know that it is not merely brands that are funding piracy by placing ads there. Ad tech companies should be reticent to where they place ads and the type of ads they accept, given that pirated services seek to make as much money as possible. We can now see that content owners and consumers are being harmed by ad companies funding piracy.
According to Unit 221B’s Chief Technology Officer Shaun Gallagher, the level of deception on pirate movie sites is alarming. Because these malware pushers prey on American consumers, they are connected to Russia. These people care nothing about the damage they cause, as they grab every last dollar they can. A few innocent clicks might result in severe violations of privacy and cost consumers hundreds of dollars, as they are bombarded with malicious ads containing ransomware and adware.”
Free culture is not the problem, cybercriminals are
There is a whole rational behind copyright infringement that is even discussed up to the United Nation. The right of humanity to enjoy and access cultural heritage is a fair and noble fight. But we must also acknowledge that Piracy website do not care about the benefits of universal access to science and culture, they only care about making money on the back of internet users.
Piracy websites, malware developers and malvertisers are creating a spectacular criminal alliance on the internet. Piracy and Streaming websites act as a bait with free movies, TV shows and live stream. Malvertisers creates a dedicated ecosystem, with on-the-shelf graphics and package, for malware developers to distributed their ransomware.


