Running a suspicious document or opening a file whose source you don’t know is always risky. However, there is a method that allows you to do this without worrying about your machine’s security. Sandbox is a Windows application that was created in 2018 in Windows 10 and is still available in Windows 11.
You can open a file in a restricted, isolated mini-environment using this tool. This software runs like any application and creates a mini-Windows in Windows, which you can then use to open unknown files without putting your computer at risk. After each use, Windows Sandbox wipes all generated data. This makes it ready for instant use again.
Despite the fact that Windows Sandbox isn’t activated by default in Windows 11, there are a few prerequisites. Moreover, the application is only available on the Professional version of Windows 11. In addition, the virtualization technology must be activated in the BIOS of the PC.
Activate the virtualization
Virtualization is already enabled on Windows 11 machines out of the box, but you can verify this by accessing your PC’s BIOS. The Virtualization Technology line (typically present in the BIOS Advanced options) indicates whether virtualization is active. If it says Enable, virtualization is active.
On your PC, you must change the Disabled setting to Enabled and then restart for the changes to take effect. If the line says Disabled, you must consult your PC manufacturer’s support to learn how to enable it. Esc, F1, F2, F8, or F10 are frequently used to access the BIOS or UEFI.
Access to Windows 11 Optional Apps and Features
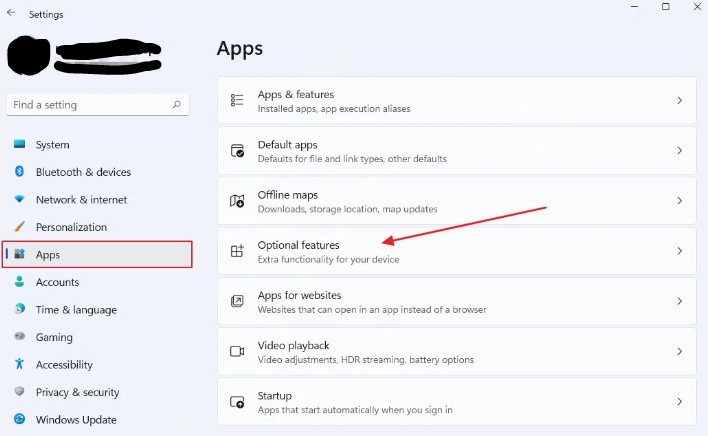
Windows 11 Pro does not come with the sandbox enabled by default. You must install it from the Windows Additional Features panel. To do so, open Windows Settings using the Windows + i shortcut, select Applications in the left column, and then click the Optional Features menu.
After you have scrolled through all the options, click on More Windows Features at the bottom of the window to continue.
Enabling Windows 11 Sandbox
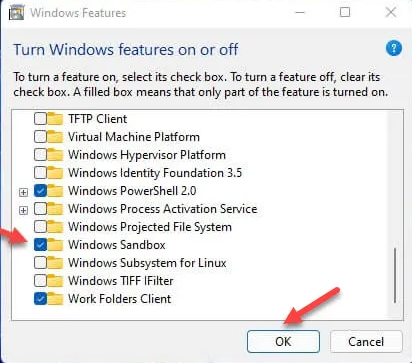
In the Windows Features panel that opens, locate the Windows Sandbox line, check the option and click the OK button to start its installation in Windows 11.
Then restart the computer.
Opening Files with the Sandbox
Open the Start menu and click on All Applications to display the list of applications installed on your PC. At the bottom of the list, open the Windows Sandbox application.
A new Windows 11 session should appear as a Sandbox panel on the screen. This session is running independently of the operating system.
You may use this session just as you would your own Windows session to browse the Web, download files, and run them with no risk.
But it is not a 100% failsafe protection. Some very advanced malwares implement
Sandbox Evasion Techniques. But for the most common malicious files, such as
ransomware, it should work.