This article is part of the Criminal Information System Management series, cybercriminal strategic positionning section.
Key Takeaways
- Porter’s Five Forces provides systematic analytical capabilities for understanding cybercriminal organizational behavior and competitive dynamics, enabling strategic defensive approaches that target structural vulnerabilities within illegal markets.
- Strategic competitive forces drive cybercriminal organizational behavior in predictable patterns that can be leveraged for defensive advantage. Cybercriminal groups face identical competitive pressures as legitimate businesses: market entry barriers, supplier negotiations, buyer demands, substitute threats, and direct rivalry.
- The professionalization of cybercrime through Corporate-like structures—exemplified by Conti’s 80-employee organization with HR departments and performance reviews— demonstrates market maturation requiring sophisticated analytical frameworks.
- State-sponsored APT groups operate under different competitive logic, prioritizing strategic persistence over immediate profit maximization, creating hybrid threat landscapes where economic and political motivations intersect.
- Defensive strategies must account for these competitive dynamics, targeting critical supply chain nodes and market disruption points rather than individual threat actors.
1. Introduction
Competitive rivalry, supplier power through specialized service providers, and lowered barriers to entry via Ransomware-as-a-Service models fundamentally drive cybercriminal innovation and organizational evolution.
The damage costs of global cybercrime economy has reached again the trillion mark in 2024 (esentire). Understanding cybercriminal organizations through traditional business frameworks reveals structured competitive forces that fundamentally shape threat actor behavior and strategic decision-making. This analysis conclude Michael Porter’s Five Forces model provides actionable intelligence for cybersecurity professionals defending against increasingly organized cyber threats, when systematically transposed to illegal markets (hbr).
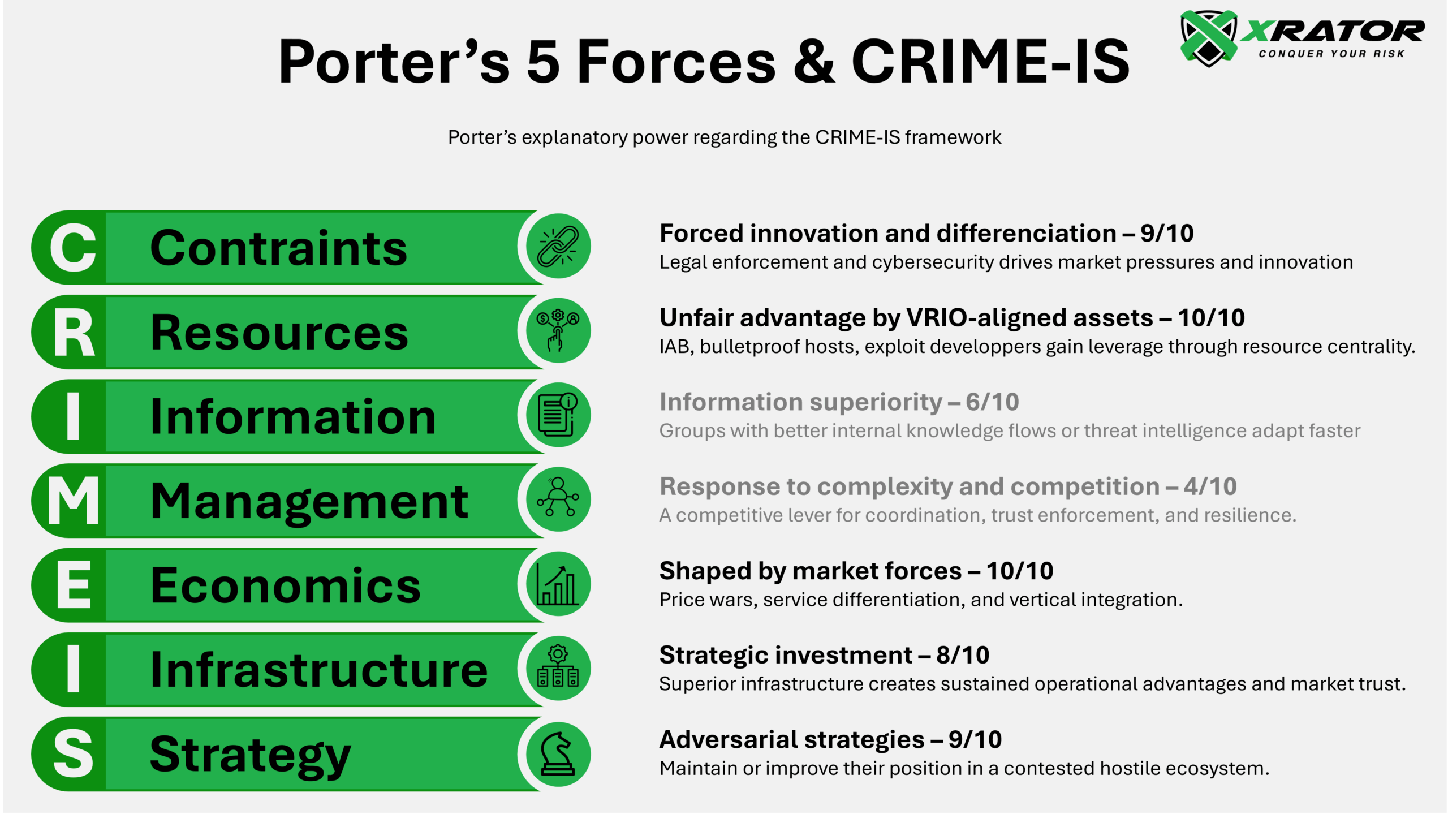
Key findings highligth that competitive rivalry, supplier power through specialized service providers, and lowered barriers to entry via Ransomware-as-a-Service models fundamentally drive cybercriminal innovation and organizational evolution.
Empirical validation from threat intelligence sources confirms that cybercriminal markets exhibit classic economic behaviors including price competition, market segmentation, and vertical integration strategies.
The research provides a systematic analytical framework combining Porter’s forces with the CRIME-IS framework (Constraints, Resources, Information, Management, Economics – Infrastructure, Strategy) to enable practical threat assessment by cybersecurity professionals.
2. Theoretical Synthesis
Michael Porter’s seminal 1979 framework established that competitive strategy emerges from understanding five fundamental forces shaping industry structure: competitive rivalry, threat of new entrants, threat of substitutes, bargaining power of suppliers, and bargaining power of buyers (hbr, timr).
Traditional applications assume legitimate market constraints: legal frameworks, regulatory oversight, and formal institutional structures. Illegal markets operate under fundamentally different conditions characterized by information asymmetries, enforcement risks, and informal governance mechanisms (etmp, ijcc, clsc). Criminal organizations function as governance institutions themselves, creating internal constraints and coordination mechanisms that substitute for absent formal institutions.
The adaptation of Porter’s framework to criminal enterprises requires acknowledging unique competitive dynamics. Academic research by Wall (2015) describes cybercriminal groups as “disorganized” assemblages rather than formal hierarchies, yet empirical evidence from threat intelligence sources reveals sophisticated organizational structures that mirror legitimate businesses (eroc, tioc, uoddocc).
The professionalization of cybercrime through Corporate-like structures demonstrates market maturation requiring sophisticated analytical frameworks. The Conti ransomware group’s (80-employee organization with HR departments and performance reviews) corporate hierarchy with specialized departments, fixed salaries, and professional HR processes exemplifies organizational complexity requiring systematic analytical frameworks (deepinstinct).
3. Transposition Analysis
Specialized service providers hold historically significant power within cybercriminal ecosystems through technical expertise concentration and infrastructure control. Yet, cybercriminal market buyers exercise increasing power through service comparison capabilities and alternative provider availability.
Competitive rivalry among cybercriminal organizations exhibits classic market behaviors including price competition, service differentiation, and market share battles. In the mean time, barriers to entry in cybercriminal markets vary significantly between profit-driven and state-sponsored organizations, with Ransomware-as-a-Service models fundamentally lowering technical barriers while maintaining reputation and capital requirements.
Cybercriminal organizations face significant substitute threats from alternative attack vectors, technology evolution, and changing target vulnerabilities.
3.1 Competitive Rivalry in Cybercriminal Markets
Darknet market analysis reveals concentrated competition with the top five markets controlling majority illegal transactions. Market share data (2024) shows Mega (22%), OMG (17%), and Solaris (13%) competing through service quality, security features, and vendor recruitment strategies (bdcc).
Price competition manifests clearly in Initial Access Broker (IAB) markets where network access prices range from $500-$3,000 with median pricing at $1,000 in 2024. (techrepublic) The 37% increase in access sales from 2021-2022 demonstrates market expansion driving competitive intensity. Service differentiation occurs through specialized targeting (48% of listings target U.S. organizations), technical sophistication levels, and customer support quality.
Competitive attacks between rival platforms demonstrate direct market warfare strategies. Organizations deploy technical attacks against competitor infrastructure while simultaneously building reputation and market share through superior service delivery(zdnet, blackfog). These exemples mirrors legitimate business competition through both direct confrontation, pricing and service excellence.
State-sponsored APT groups operate under different competitive logic, with rivalry focused on strategic intelligence value rather than immediate profit maximization. China-linked APT activity surged 150% across all sectors in 2024 (SecurityWeek), demonstrating competitive escalation between nation-state actors already pursuing similar objectives across overlapping target sets (enisa, xrator, eset, sentinelone).
3.2 Threat of New Entrants
Traditional barriers include technical expertise requirements, infrastructure development costs, and trust-building in anonymous markets (cf ijlc, clcc). The evolution of RaaS business models democratizes cybercrime participation by providing complete operational frameworks to affiliates. Revenue sharing models (20-30% to developers, 70-80% to affiliates) reduce initial capital requirements while providing access to sophisticated technical capabilities (arkoselabs, eastgate).
In 2020, REvil deposited $1 million in Bitcoin on forums specifically to attract skilled affiliates, demonstrating active barrier reduction strategies (ibm). Significant entry barriers persist through reputation requirements in trust-scarce illegal markets (pubc). Cybercriminal organizations must demonstrate reliability, technical competence, and operational security before gaining access to high-value opportunities (hfcc). Initial reputation building often requires months of lower-value activities to establish credibility within criminal networks.
Capital requirements vary dramatically between attack types. Simple phishing operations require minimal investment while sophisticated APT campaigns demand substantial infrastructure development, zero-day exploit acquisition, and sustained operational funding. Lazarus Group’s estimated billions heists in cryptocurrency thefts demonstrates the resource advantage of established organizations over new entrants (cyberscoop).
3.3 Bargaining Power of Suppliers
Initial Access Brokers (IAB) markets demonstrate classic supplier concentration effects with specialized vendors controlling access to specific geographic regions or industry sectors. The 48% focus on U.S. organizations creates geographic specialization that increases individual supplier leverage. Price stability around $1,000 median suggests suppliers maintain pricing power despite increased competition. (socradar, hackernews) Initial Access Brokers exemplify high supplier power through specialized network compromise capabilities that enable entire criminal operations.
Technical service suppliers including malware developers, exploit authors, and infrastructure providers command premium pricing through specialized expertise (zdnet2). Bulletproof hosting providers have significant power by controlling essential infrastructure that cybercriminal operations cannot easily substitute (infosecuritymag). Cryptocurrency laundering services represent another high-power supplier category through regulatory complexity and technical sophistication requirements. (europol)
State-sponsored APT groups often develop internal capabilities to reduce supplier dependence, but still rely on specialized contractors for specific technical requirements. APT41’s hybrid structure demonstrates how state-sponsored groups balance internal development with external service procurement to maintain operational flexibility (googlecloud).
3.4 Bargaining Power of Buyers
Ransomware affiliates can evaluate multiple RaaS offerings based on success rates, technical capabilities, customer support quality, and revenue sharing terms (paloalto). The sophistication of cybercriminal buyers has increased substantially, with affiliates conducting due diligence on RaaS providers through reputation research, technical capability assessment, and operational security evaluation (xrator2). Multiple provider options create competitive pressure that benefits buyers through improved services and competitive pricing.
Large-scale buyers in cybercriminal markets often possess significant negotiating power through volume purchasing and exclusive partnership opportunities (ptsecurity). However, buyer power remains constrained by trust requirements and operational security concerns. Anonymous market conditions limit buyers’ ability to enforce agreements or pursue remediation for unsatisfactory services, maintaining some supplier advantage in buyer-supplier relationships. (cpp, usenix).
Vendor verification and reputation systems—such as review scores, comment sections, and star ratings—are widely used to help buyers assess trustworthiness (tue). However, because these markets are saturated with competing sellers and new entrants, it is challenging for any vendor to stand out and accumulate enough positive feedback to be considered highly reputable (jie). Escrow providers must also build a reputation for reliability, which is difficult given the risks of exit scams, platform shutdowns, and the temptation for even long-standing guarantors to abscond with funds (reliaquest).
3.5 Threat of Substitutes
Traditional ransomware groups now compete with data theft and extortion models that achieve similar revenue outcomes through different methodologies (cyr). Technology evolution creates continuous substitute pressure as defensive improvements render specific attack types less effective.
Cryptocurrency-focused attacks represent substitutes for traditional financial cybercrime as blockchain technology creates new high-value targets. While the total volume of traditional financial cybercrime remains higher, the average value per cryptocurrency attack is increasing, and the overall threat is escalating rapidly. In 2025 alone, over $2.1 billion was stolen in just the first half of the year, with the average theft size rising to $30 million (aiinvest).
State-sponsored APT groups face substitute threats from alternative intelligence collection methods including human intelligence, signals intelligence, and open source intelligence gathering (google). However, cyber operations often provide unique access to specific target categories that limit effective substitution options.
Also, alternative criminal activities compete for skilled personnel and organizational resources (baffi). Traditional organized crime, legitimate technology employment, and other illegal activities create substitute attraction for potential cybercriminal participants, particularly during law enforcement pressure periods (vunl, occrp).
4. Criminal Modeling
Profit-driven cybercriminal organizations exhibit sophisticated business models with clear organizational structures (not necessarily hierarchical), performance management systems, and strategic planning capabilities. As for state-sponsored APT groups, they seem to operate under hybrid organizational models combining military structure with entrepreneurial flexibility to achieve strategic objectives while generating revenue for state sponsors.
Emerging hybrid models should be considered seriously. They combine state strategic objectives with criminal profit incentives, creating complex competitive dynamics that blur traditional categorization boundaries.
4.1 Profit-Driven Cybercriminal Organizations
Conti’s organizational structure demonstrates professional management practices including fixed wages ($1,800-$2,500 monthly) rather than percentage-based compensation, performance reviews, and employee handbooks. Monthly operational costs of $140,000-$165,000 reveal substantial organizational overhead comparable to legitimate technology companies (cf deepinstinct). Same structuration as been observed in FIN7 for example (prodaft).
Revenue models vary across cybercriminal organizations with RaaS providers typically claiming 20-30% of successful attack proceeds while affiliates retain 70-80%. REvil’s estimated $81-123 million in profits during 2020 demonstrates the scale of sophisticated cybercriminal operations (csoonline).
Market positioning strategies include geographic specialization, industry vertical focus, and technical capability differentiation (socioox, forbes, blackfog2). Organizations compete through attack success rates, technical sophistication, and customer support quality rather than pure price competition (experian, ecoinfosec, bnkis) . This demonstrates market maturation toward service quality differentiation.
Innovation investment focuses on evasion technique development, attack automation, and customer service quality improvement (policinginsight, darktrace, ciab).
4.2 State-Sponsored APT Organizations
Lazarus Umbrella multi-subgroup structure, Shinese-nexus, GOSSIPGIRL Supra Threat Actor or Iran’s cyber organization demonstrates sophisticated organizational complexity (stanford, sekoia, sekoia2, chronicle). Lazarus’ dual mission combining state espionage with financial cybercrime creates unique competitive advantages through resource availability and strategic patience. APT38/BlueNoroff subgroup’s approximately 1,700 members represents substantial organizational scale focused on financial institution targeting. (europeoc)
Geographic distribution and operational timing often reflect state sponsor constraints rather than market optimization. APT1’s Shanghai-based operations following Beijing business hours demonstrates how state organizational requirements influence cybercriminal operational patterns (mandiant).Target selection balances strategic intelligence value with financial opportunity assessment.
Resource allocation follows strategic priorities with substantial investment in zero-day exploit development, advanced persistent access maintenance, and long-term target relationship development (dailyswig, mandiant, symantec). Long infiltration lasting 4 years 10 months demonstrates strategic patience unavailable to purely profit-driven organizations (recordedfuture).
4.3 Hybrid Models and Market Evolution
The Appin/Belltrox case in India, NSA cyber contractors developping malware, APT41’s contractor relationship with Chinese state interests while conducting independent profit-driven operations exemplifies an evolution toward hybrid model where legitimate companies may buy resources to cybercriminal to perform cyber operation for state sponsor (intelligenceonline, guardian, google2).
These hybrid models create competitive advantages through dual revenue streams, strategic patience for high-value targets, and technical capability sharing between state and criminal objectives. Tacit state approval for criminal activities alongside strategic objectives enables risk-taking unavailable to purely commercial operations (usdoj, globalinitiative, csis).
Market evolution trends indicate increasing professionalization across all cybercriminal organization types with adoption of legitimate business practices, formal organizational structures, and strategic planning processes (nature). This maturation creates opportunities for defensive strategies targeting business-critical functions and competitive vulnerabilities.
5. Edge cases
Emerging cooperation models between profit-driven cybercriminals and state sponsors create complex competitive dynamics that challenge traditional analytical frameworks. Also, increasing integration between cybercriminal organizations and legitimate businesses creates complex competitive boundaries and analytical challenges. Finally, Artificial Intelligence (AI) integration creates unprecedented competitive dynamics within cybercriminal markets through both offensive logistics enhancement and defensive technology improvement.
5.1 Cybercriminal-State Cooperation Models
Cybercriminal-State Cooperation is well exemplifies with the Russo-Ukrainian war or the Israel/Iran war, where groups operating with tacit state approval while maintaining independent profit objectives (globalinitiative, cyr2).
State tolerance for cybercriminal activities targeting foreign entities creates unique competitive advantages through reduced law enforcement pressure domestically while maintaining international targeting capabilities (businessinsider, cepa, ). This cooperation model enables cybercriminal organizations to scale operations beyond pure market constraints while providing states with more than plausible deniability for strategic operations (cyr3).
However, these relationships also create dependencies and constraints that limit organizational flexibility and efficiency (joc). State sponsor priorities may conflict with profit optimization, creating strategic tensions within hybrid organizational models (jnslp). The potential for state enforcement action maintains uncertainty that influences competitive behavior and strategic planning.
5.2 Legitimate Business Integration
Professional enablers including legal counsel, financial advisors, and technology consultants increasingly serve both legitimate and criminal clients (lawsociety, brisbanetimes, tbjc). This integration enables cybercriminal organizations to access sophisticated business services while maintaining operational security through compartmentalization. Legitimate business acquisition by criminal organizations provides cover for illegal activities while generating legal revenue streams (googlecloud2). These hybrid models complicate competitive analysis by blending legal and illegal competitive forces.
Regulatory responses to this integration create new competitive pressures through enhanced due diligence requirements, compliance monitoring, and enforcement actions (cf lawsociety). Organizations must balance operational effectiveness with regulatory risk management, creating additional competitive dimensions beyond traditional market forces (tcnews, mckinsey).
5.3 Technology Disruption Impact
AI-powered attack automation reduces personnel requirements while increasing technical sophistication levels (kaspersky, uiuc,ijfmr). Simultaneously, AI-enhanced defensive technologies create substitute pressures by reducing attack success rates and increasing detection capabilities (microsoft, gsj, ). This technology arms race ponts to how external innovation disrupts established competitive advantages and forces organizational adaptation (nott, icars).
Quantum computing development represents a potential future disruption that could fundamentally alter cybercriminal competitive dynamics through encryption breaking capabilities and defensive quantum technologies (europol, ecis, ).
Any organizations must balance current competitive optimization with future technology transition planning.
6. Practical Implementation
Step 1: Competitive Landscape Assessment
(2-4 weeks initial, 2 hours monthly updates)
Using existing incident data and vendor reports, categorize active threat groups:
- Market Leaders (>30% of your incidents): Deep strategic analysis priority
- Major Competitors (10-30%): Regular assessment and monitoring
- Niche Players (<10%): Specialized threat evaluation
- New Entrants: Emerging groups requiring classification
Assessment Framework: For each group, document competitive strategy (cost leadership vs. premium capabilities vs. niche focus), current trend (growing/stable/declining), and primary competitive pressures (law enforcement, technical countermeasures, rival groups).
Step 2: Critical Supplier Identification
(1-2 weeks, integrate with existing collection)
Map threat enablers by impact and disruption difficulty:
- High-Impact Suppliers: Initial Access Brokers, specialized infrastructure providers
- Medium-Impact: Standard hosting, commodity tools, support services
- Priority Targets: High impact + low disruption difficulty
Step 3: Strategic Decision Prediction
(15-30 minutes per significant event)
When threat groups face pressure, assess likely responses using historical patterns and resource constraints. Track prediction accuracy to refine methodology.
Resource Requirements: 20% additional analyst time initially, 5% ongoing. Integrates with existing collection sources (no new tools required).
CISO Consideration
Enhanced Risk Assessment: Predict threat evolution vs. react to attacks
Strategic Resource Allocation: Target defenses against sustainable criminal competitive advantages
Executive Communication: Business-context threat briefings with trend analysis
Legal support: Coordinate with legal team on intelligence sharing boundaries and ensure compliance with competitive intelligence best practices.
Monthly Executive Deliverable: One-page competitive threat landscape showing market position changes, disruption opportunities, and strategic predictions with confidence levels.
Success Metrics: Track prediction accuracy and early warning value versus traditional indicators.
7. Conclusion
This systematic application of Porter’s Five Forces to cybercriminal organizational analysis demonstrates that competitive market dynamics fundamentally shape threat actor behavior across all dimensions of the CRIME-IS framework, with weakness when it comes to model internal process.
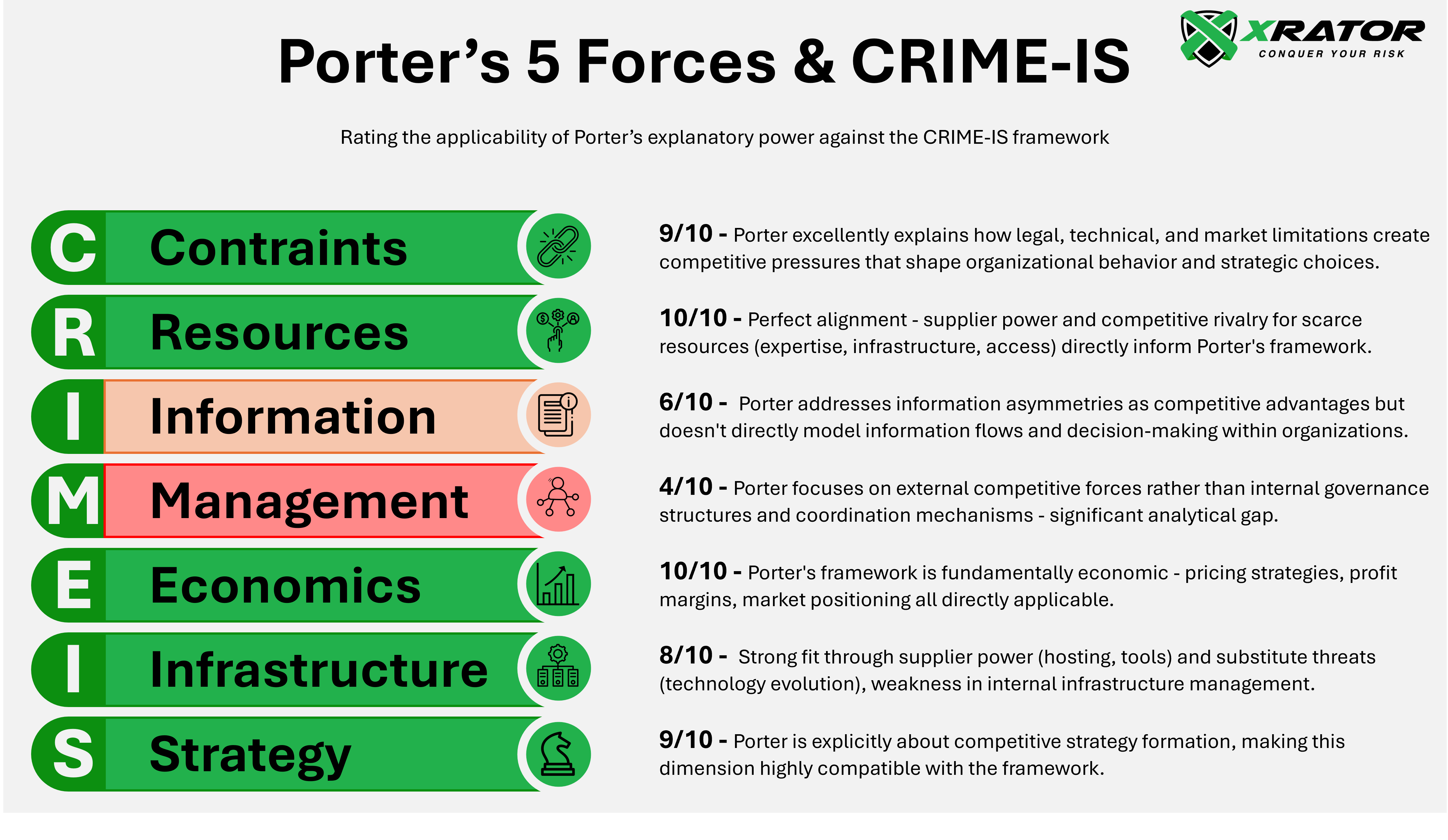
The four-dimensional transposition model confirms Porter’s framework applicability across organizational aspects. Porter’s market-focused approach struggles with Structural and Processual dimensions, as it examines external competitive forces rather than internal organizational design and workflow management.
- Structural analysis reveals how competitive forces shape organizational hierarchies, from flat networks competing on agility to formal structures competing on reliability.
- Processual analysis demonstrates competitive standardization, with successful groups systematizing operations to maintain market advantages.
- Technological analysis shows how competitive pressure drives technical innovation cycles.
- Human analysis reveals talent competition and recruitment strategies that mirror legitimate industry patterns.
Porter’s competitive forces operate differently across the five-level cyber threat actor taxonomy, providing structured analytical capabilities for threat intelligence practitioners.
- Level 1 individual criminals face primarily substitute threats and low entry barriers. Porter’s power is rather weak here. Cybercrime has limited competitive dynamics as individuals rarely experience market forces. Also, even if “solo-operator” APT is possible, it requiere a organizational backing.
- Level 2 criminal groups experience increased competitive rivalry and supplier dependencies. Porter’s power is moderate. For-provit actors display some competitive pressure for resources and targets. Mission assignement and limited resources rivalry reduce competition for APT actors.
- Level 3 criminal organizations demonstrate full competitive force interaction, with sophisticated responses to buyer power and supplier negotiations. Porter’s power is strong. Clear competitive market dynamics and strategic positioning on the cybercrime side. For state-sponsored organizations resource competition exists but strategic objectives override pure market forces.
- Level 4 criminal ecosystems exhibit complex inter-organizational competitive dynamics where Porter’s forces operate simultaneously across multiple organizational boundaries. Porter’s power is very strong. Cybercrime ecosystems have complex inter-organizational competition and cooperation, while APT face significant competition for strategic influence and intelligence value.
- Level 5 Crime-as-a-Service platforms represent mature market structures where competitive forces drive continuous innovation and service quality improvement. Porter display a perfect match for profit-driven platform : pure market dynamics with service competition. On the intelligence side, hybrid models blur competitive logic between state and criminal objectives.
Each level requires adapted analytical approaches while maintaining consistent competitive intelligence frameworks. Cybercriminals operate in genuine markets with profit maximization, price competition, and customer satisfaction dynamics, making Porter’s framework highly relevant. APTs pursue strategic objectives where “success” is measured in intelligence value, geopolitical influence, or mission accomplishment rather than financial returns.
The five-level taxonomy remains relevant but requires acknowledging that modern threats often span multiple levels simultaneously – a single APT campaign might involve Level 5 platform utilization, Level 3 organizational structure, and Level 2 criminal contractor groups.
For researchers, game-theoretic modeling of cybercriminal competitive interactions can provide insights into strategic decision-making processes and equilibrium outcomes. Understanding how competitive forces influence cybercriminal investment decisions, target selection, and organizational structure enables more effective countermeasures. Network analysis combined with competitive intelligence can reveal structural relationships within cybercriminal ecosystems. Social network analysis of cybercriminal organizations can identify critical nodes and relationship patterns that inform disruption strategies.
Our next article will examines Oliver Williamson’s Transaction Cost Theory (TCT).


