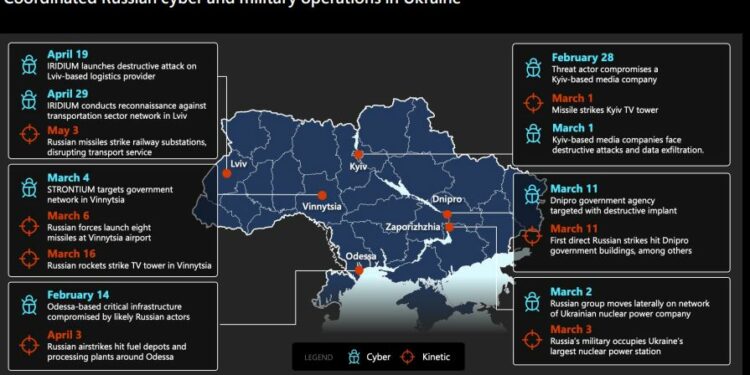
On several occasions the Russian military has coupled its cyberattacks with conventional weapons aimed at the same targets.
🚩The Ukraine-Russia war is unique in our modern history, as it is the first time at the age of digitalization that the full spectrum of conventional and unconventional strategical powers is deployed by or against a Security Council member (Structural Power, 1982, Susan Strange) :
- Military, security & intelligence
- Industry and logistics
- Economy, Currency & Credit
- Communication, Influence and Knowledge
- Citizen Welfare
- Energy and raw materials
🎙️Brad Smith (President and Vice Chairman at Microsoft) highlight another uniqueness. In its opening of Microsoft’s report, “Defending Ukraine : Early Lessons from the Cyber War” : “The recorded history of every war typically includes an account of the first shots fired and who witnessed them.”
And the first shot in our case was a malicious software : FoxBlade.
💡Five key takeaways :
- Defense against a military invasion now requires the use of digital operation
- Cybersecurity is mandatory in a nation defensive toolbox
- Espionnage operations can project themselves quickly and quietly outside the war zone using Internet
- Cyberattacks and Influence operations goes hand-in-hand
- Entanglement of Physical, computerized and cognitive offensive operations that are supporting one another. Defensive strategies must consider this coordination and treating them together without analytical silos.
In April 2022, cybersecurity authorities of the United States, Australia, Canada, New Zealand, and the United Kingdom released a joint publication. The report said that Russian government-sponsored cyber attacks are increasing with both the involvement of cybercrime gang and intelligence agencies. The potential cyberattacks can target organizations or countries other than Ukraine, including destructive malware, ransomware, DDoS attacks, and cyber espionage.
In may 2022, one of such affiliated cybercrime gang attacked Lithuanian websites and the government of Costa Rica in retaliation to their support to Ukraine. They impacted the country’s foreign trade by disrupting its customs and taxes platforms by breaking into Costa Rica’s Ministry of Finance.